CyLock MFA for Remote Access
Enabling MFA is a vital part of any remote access security strategy as it can provide better security for remote access of resources. Accessing resources from outside is never a challenge, as many hardware / software based VPNs provide multiple ways to allow users to access corporate data. But there is a critical need to balance security with ease of use. Any system involving carrying external hardware for authentication purposes can be uncomfortable and makes user adoption challenging.
Considering many factors CyLock enables MFA for remote access software by leveraging what the user already has and can easily access – their smartphone combined with PIN/ fingerprint making it a convenient experience for employees.
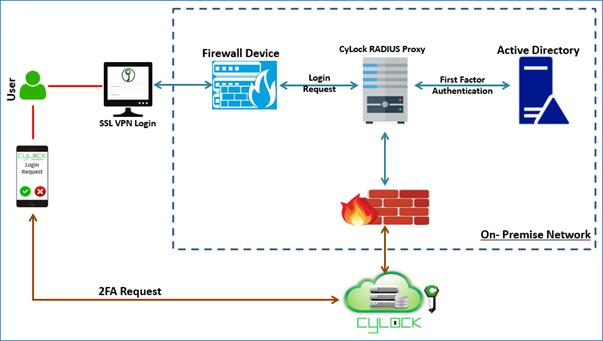
CyLock provides a strong Multi-Factor Authentication to remote access software provided by VPN devices or software through RADIUS protocol. CyLock protects logins to SSL VPNs using a variety of authentication methods, including PUSH notification, CR-OTP and software tokens using end users mobile devices. CyLock Authentication Proxy component can be deployed in an on premise server to enable MFA for SSL VPN provided by firewall devices or software based VPNs using the RADIUS authentication protocol.
CyLock Supports Local User
CyLock RADIUS Proxy authenticates the first factors against AD / LDAP deployed in the on-premise or cloud. But there is a growing need for organizations to authenticate local users who are not part of the AD / LDAP like external vendors, consultants etc., as they are often left out of MFA policy. This can pose a serious threat to resources in an organization. CyLock allows complete management of local users through its portal, using which administrators can create, update, delete and enable MFA policies for them while accessing SSL VPN thereby mitigating the security risks.
Authentication Options
On top of strong password policies, organizations can enable MFA to provide a more secure SSL VPN login process within the organization. MFA can provide security against cyber-attacks thereby safeguarding enterprise identity and data. The table below lists the authentication types and the security options supported during SSL VPN.
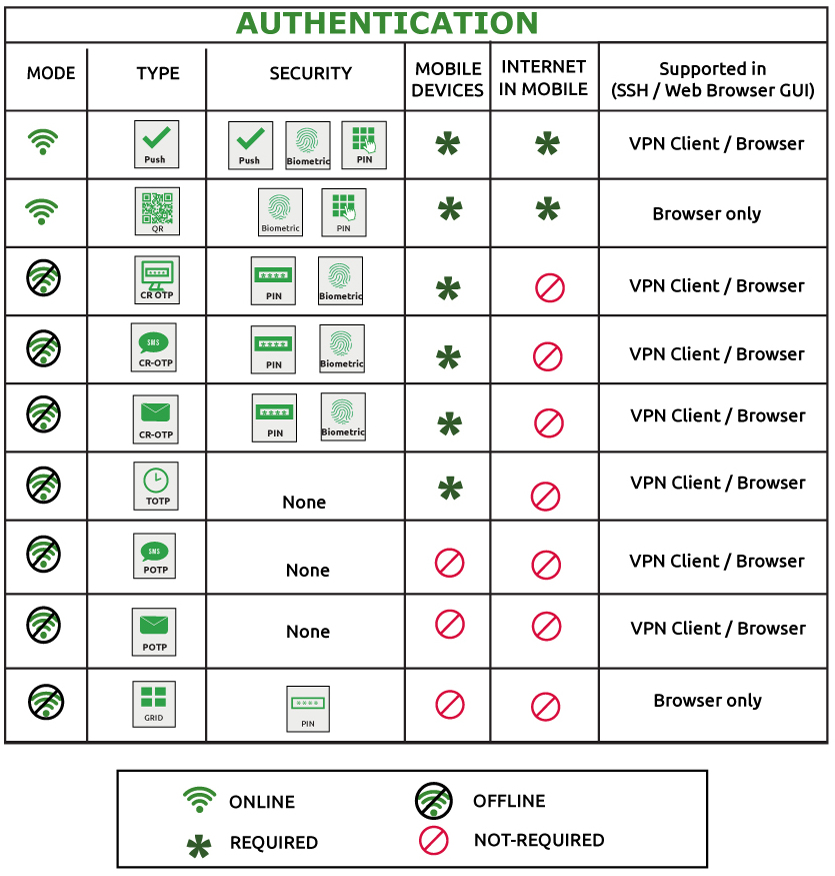
Most of the authentication options are available while logging in through a VPN client except for QR and GRID authentication.
Currently CyLock supports MFA for SSL VPN for the below hardware / software:
-
Array AG SSL VPN
-
Fortinet FortiGate SSL VPN
-
SonicWall SSL VPN
-
Sophos SSL VPN
-
Palo Alto SSL VPN
-
Cisco ASA SSL VPN
-
SSL VPN using OpenVPN software
Benefits of enabling CyLock MFA for SSL VPN
-
Complies with regulatory standards for safeguarding sensitive data
-
Provides assurance on the users accessing your organization’s network
-
Only valid and verified users can access organization resources through SSL VPN
-
Enables MFA for every user - be it AD / LDAP or Local users
-
Defend against modern threats like phishing, SIM Swap etc.
-
Seamless integration and deployment convenience
Looking at securing your SSL VPN logins? Contact us today to learn more about how we can secure your SSL VPN logins.