What is Single Sign-On (SSO)?
Single Sign-On (SSO) is an authentication process that enables users to access multiple applications and systems using a single set of credentials (username and password). Instead of logging into each application separately, SSO allows users to authenticate once and gain access to all connected applications - reducing password fatigue, improving productivity, and strengthening security posture.
How Does SSO Work?
SSO works by establishing trust between the Identity Provider (IdP) — which authenticates users — and multiple Service Providers (SPs) — the applications the user wants to access. Once a user authenticates with the IdP, a secure token is exchanged between the IdP and SP, allowing access without repeated logins.

Typical SSO Workflow
-
User Request: The user attempts to access an application (Service Provider).
-
Redirection to IdP: The application redirects the user to the Identity Provider (CyLock IdP, ADFS etc.,) for authentication.
-
User Authentication: The user provides credentials and complete MFA.
-
Token Issuance: Upon successful authentication, the IdP sends a signed token (SAML assertion / OAuth token / OpenID token) to the application.
-
Access Granted: The application validates the token and grants access to the user.
Core Components of SSO
-
Identity Provider (IdP): Authenticates users and issues secure tokens (SAML, OAuth, OIDC) to connected applications. CyLock IdP acts as a centralized authority, seamlessly integrating with Active Directory, LDAP, and cloud directories. Built-in MFA strengthens security and enables unified access to all applications.
-
Service Provider (SP): Any application or service that relies on an Identity Provider to authenticate users. The SP trusts the IdP to validate users and accepts the authentication token provided (Ex: Microsoft 365, VMWare Cloud director etc.)
-
Authentication Protocols: Standards like SAML, OAuth, and OpenID Connect enable secure, interoperable token exchange between IdP and SP.
-
User Directory: Stores user credentials and attributes (Ex: AD, LDAP etc.) to manage identities centrally.
CyLock IdP is the powerhouse behind seamless Single Sign-On, robust Multi-Factor Authentication, and unified user management. It acts as the central control point for authenticating users, enforcing security policies, and granting secure access to all enterprise applications — whether on-premises, in the cloud, or in hybrid environments. With CyLock IdP, organizations can simplify identity management, strengthen security, and deliver a smooth, consistent access experience for employees, partners, and customers alike.
Benefits of CyLock SSO
-
Reduces password fatigue by minimizing the number of passwords users need to remember.
-
Speeds up user access to multiple applications with a single login, improving productivity.
-
Lowers IT helpdesk costs by reducing password reset requests.
-
Enhances security with centralized authentication, stronger policies, and reduced password reuse risks.
-
Simplifies access management, including user provisioning and de-provisioning.
-
Supports compliance by enabling consistent security controls and detailed audit trails.
-
Enables seamless integration with both cloud and on-premises applications.
-
Improves user experience with faster, smoother workflows.
-
Supports modern authentication methods like MFA, biometrics etc.
-
Increases adoption of enterprise applications by removing login barriers.
Seamless and fast access to internal or external work applications without the need of remembering multiple passwords or logging into individual applications significantly improves employee productivity. CyLock SSO, enabled with strong security measures, makes this possible by delivering a smooth and secure user experience.
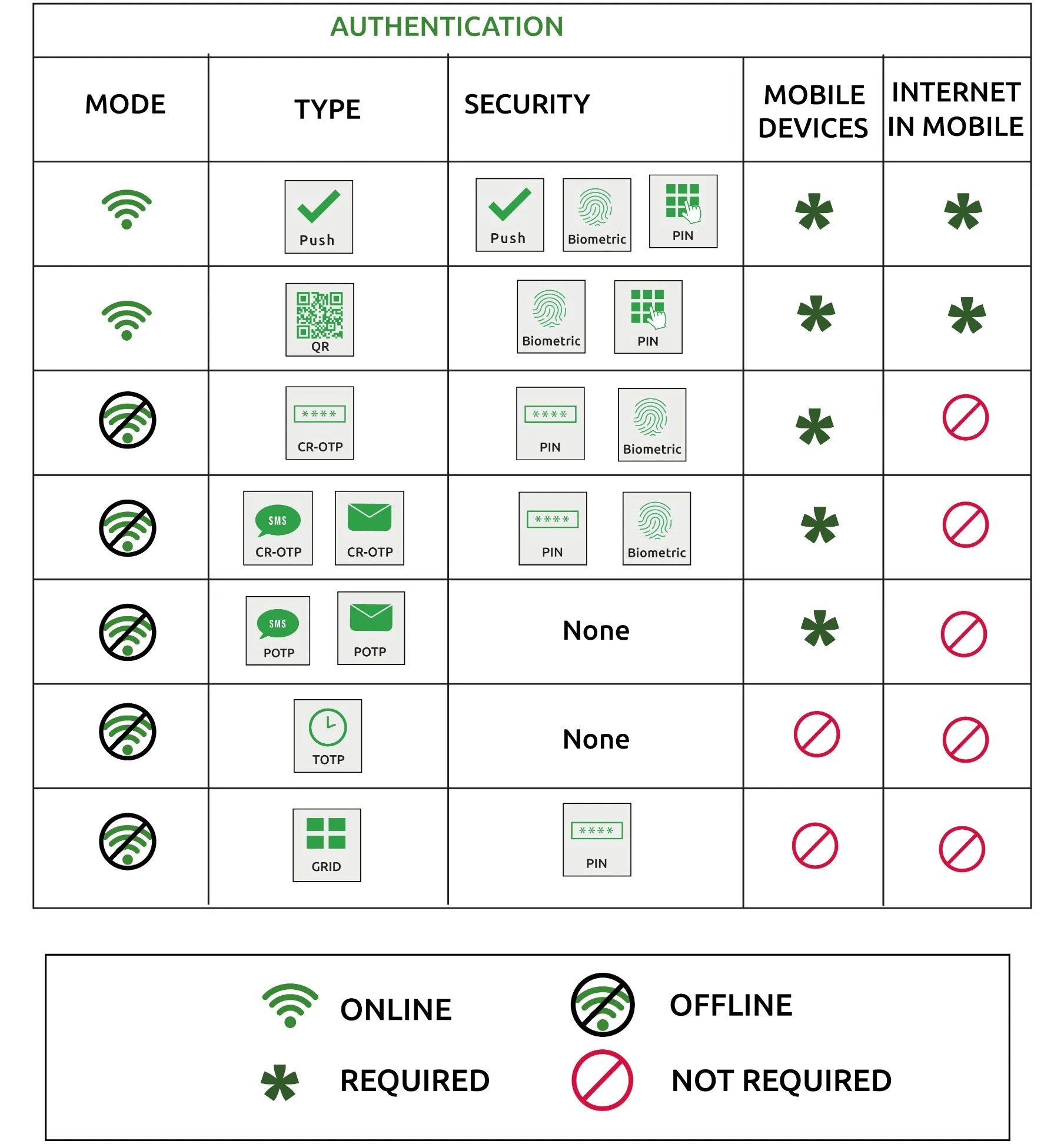
CyLock SSO Security
On top of strong password policies, organizations can enable MFA to provide a more secure SSO process within the organization. MFA can provide security against cyber-attacks thereby safeguarding enterprise identity and data. The table below lists the authentication types and the security options supported during SSO.
SSO Use Cases & Scenarios
-
Workforce Productivity: Empower employees with unified access to business-critical tools like CRM, HRMS, and email for faster workflows.
-
Partner & Customer Portals:Simplify authentication for external users accessing partner, customer, or vendor portals securely.
-
Education Access:Provide students, faculty, and staff with one-click access to learning management systems (LMS), libraries, and campus services.
-
Cloud & SaaS Applications:Secure and streamline access to cloud apps like Microsoft 365, VMWare Cloud Director, and more.
-
Remote Workforce Enablement:Allow employees to securely access enterprise applications anytime, from anywhere, with ease.
Supported Protocols
CyLock SSO offers flexible integrations by supporting all major SSO protocols to fit into any IT ecosystem — modern, legacy, cloud, or on-premises.
-
SAML 2.0: XML-based standard for web SSO, enabling one-time authentication to access multiple enterprise apps like CRMs, HR systems, and intranets.
-
OAuth 2.0: Token-based framework for secure API and app access without sharing passwords, ideal for cloud apps and micro services.
-
OpenID Connect (OIDC): Adds authentication to OAuth 2.0, using lightweight JWT tokens for fast, secure login to modern web and mobile apps.
-
LDAP & Active Directory: Integrates with enterprise directories, allowing users to authenticate with existing credentials across cloud and on-prem apps
Why Choose CyLock SSO?
Cylock SSO stands out with a secure, flexible, and scalable platform built for modern enterprises.
-
Broad Protocol Support: Connect seamlessly with virtually any cloud, on-premises, or legacy application using industry-standard protocols.
-
Flexible Deployment Options: Connect Deploy in the cloud, on-premises, or hybrid environments — whatever fits your IT strategy.
-
Customizable User Experience: Connect Brand your login portals to reflect your organization’s identity for a consistent, trusted experience.
-
Deep Visibility & Analytics: Connect Monitor access events and user activity with rich insights for better security and compliance.
-
Built-in MFA for Stronger Security: Enhance protection effortlessly with CyLock’s advanced Multi-Factor Authentication.
-
Effortless Scalability: Whether you’re a small business or a global enterprise, CyLock scales to meet your growing needs.
Powered by CyLock IdP — Your Gateway to Secure, Unified Access
Behind every secure and seamless login is CyLock’s powerful Identity Provider (IdP) — the core engine driving our SSO, MFA, and user management. Engineered for flexibility and security, CyLock IdP ensures smooth access across all your applications, no matter where they reside.
Frequently Asked Questions
Here's the breakdown:
1. Centralised Hub: An SSO provider, like CyLock, acts as a central login portal.
2. Trusted Apps: Apps you use connect to the SSO provider, forming a secure trust chain.
3. One Login, Many Doors: You log in once with your credentials, and the SSO provider verifies your identity.
4. Secure Token: The provider then grants a secure token, allowing access to connected apps without needing separate logins
- Security:Less chance of breaches due to weak or reused passwords.
- Efficiency:Saves time and frustration with faster logins.
- Compliance:Meets stricter regulations for data access.
- Management:Simplifies user access control and IT administration.

