Overview
CyLock MFA enables strong Multi-Factor Authentication for any Array AG Series Device based SSL VPN user login. CyLock MFA integrates with the Array AG Device through CyLock MFA RADIUS proxy component installed in a server within the organization’s local network.The CyLock MFA RADIUS proxy component enables any Array AG Series Device with RADIUS protocol support to carry out a strong Multi-Factor Authentication (MFA) during remote login to remote network through SSL VPN.
Architecture Overview
CyLock MFA RADIUS proxy component needs to be installed within your network to enable MFA during SSL VPN login process. First factor (user login credentials) can be authenticated with an on-premise AD / LDAP / LDAP Server or against CyLock MFA local store. A typical deployment architecture and process is shown below.
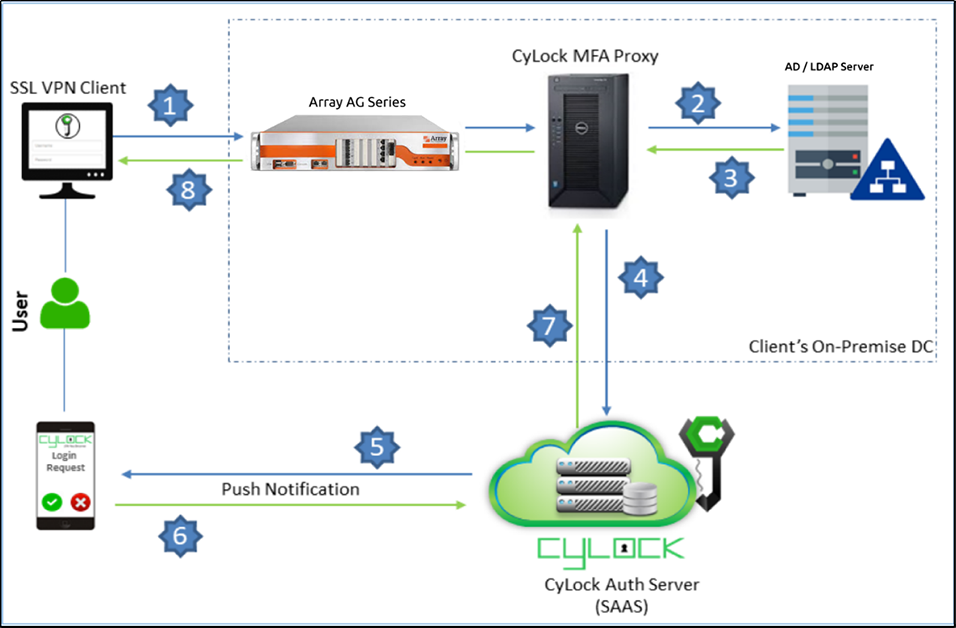
Figure 1 – Deployment Architecture Block diagram of integrating Fortinet Firewall with CyLock RADIUS Proxy
Note:
- CyLock MFA RADIUS Proxy communicates with CyLock MFA Auth Server on TCP port 443
- Any firewall configuration to restrict access to CyLock MFA Auth Server through destination IP address or IP address ranges is not recommended as the IP addresses may change to provide service high availability
Prerequisites
- Securing an application requires an active CyLock MFA account. (Refer “Getting Started: Guide to CyLock MFA” to start using CyLock MFA to protect your applications)
- Login to “CyLock MFA Portal”
- Navigate to Application menu in the left menu panel
- Click “Add Application” button to secure an application. Locate and select “SSL VPN” from the list of application names. Click “+Secure” button to configure CyLock MFA for SSL VPN. Enter the details as requested and click “Save” button. Before leaving the page copy API Key and Customer ID, which are required during CyLock MFA RADIUS Proxy component installation. See “Securing an application” for more information about protecting applications in CyLock MFA
- Node.JS to be installed in the server where the CyLock MFA RADIUS Proxy component will be deployed
- Download the CyLock MFA RADIUS Proxy component
- Download the CyLock Theme from the URL
- Follow the instructions in “CyLock MFA RADIUS Proxy Installation” section to enable Multi-Factor Authentication (MFA) for SSL VPN user login
- Verify Microsoft AD / LDAP or LDAP Server is installed and configured for authenticating first factors of users
- Download CyLock MFA Mobile App from Play Store or iOS store
- Register SSL VPN user using CyLock MFA Mobile app.
CyLock MFA RADIUS Proxy Installation
CyLock MFA RADIUS Proxy component will receive incoming RADIUS requests from your Array AG Device during SSL VPN login. The proxy component will then perform the primary authentication (first factor authentication) either with your internal AD / LDAP server / LDAP Server or CyLock MFA local store, and then contact CyLock MFA Auth server for second factor authentication.
CyLock MFA RADIUS Proxy can be installed on a physical or virtual host within your network. We recommend a system with at least 4 vCPU, 200 MB disk space, and 4 GB RAM. CyLock MFA RADIUS Proxy supports the following operating systems:
- Windows Server 2008 or later (Server 2016+ recommended)
- CentOS 7 or later (CentOS 8+ recommended)
- Red Hat Enterprise Linux 7 or later (RHEL 8+ recommended)
- Ubuntu 18.04 or later (Ubuntu 20.04+ recommended)
- Debian 7 or later (Debian 9+ recommended)
Install Node.JS in the server where the CyLock MFA RADIUS Proxy component will be installed.
Download the CyLock MFA RADIUS Proxy component. Refer Prerequisites section above. After downloading, copy/move the Proxy Component to the respective server.
Configuring CyLock MFA RADIUS Proxy component
Go to the folder where the Proxy component has been copied. Extract the CyLock_radius_proxy.zip. After extracting, follow the below steps to configure the component.
On Windows or Linux machine go to the respective folder where the proxy component was copied & extracted.
MFA Configuration:
Open the cyconfig.js file in CyRadius Folder with administrative privileges and change the below Properties.
| # |
Property Name (key) |
Description (value) |
| 1 |
url |
Enter Auth URL (Ex - https://demoauth.cybernexa.com/api/v2/srv/)
Contact the CyLock Support Team to get the Auth Server URL.
|
| 2 |
id_sp |
Customer ID value. Refer point #4 in Prerequisites section. |
| 3 |
Authorization |
API Key value. Refer point #4 in Prerequisites section. |
| 4 |
radius_secret |
Paste the Encrypted Radius secret key.
To obtain the encrypted RADIUS Secret key, please refer to the Key Encryption Process Section listed below.
|
Note: Do not modify the key in the key-value pair.
AD / LDAP Configuration:
To enable RADIUS Proxy component, communicate with MS AD / LDAP server or LDAP server, configure the adconfig.js file.
Open the adconfig.js file in CyRadius Folder with administrative privileges and change the below properties.
| # |
Property Name (key) |
Description (value) |
| 1 |
Open_ldap_server |
Enter your open ldap server URL (ex: ldaps://ldap.cybernexa.com)
|
| 2 |
domain |
Provide your AD / LDAP domain name. |
| 3 |
url |
For secured LDAP:
ldaps://computername.domain.com or else simply use
For normal LDAP:
ldap://computername.domain.com
|
| 4 |
baseDN |
Domain name |
| 5 |
password |
Paste Your AD / LDAP server Administrator user’s Encrypted password. To obtain the encrypted AD / LDAP Password, please refer to the Key Encryption Process Section listed below. |
Key Encryption Process:
Encrypting RADIUS Secret Key and AD / LDAP Password.
a. After Unzip the radius_proxy.zip file. Go to the secure_cred directory and execute the "secure_cred.js" file using the command below
- Enter Customer ID (ID_SP): Get the ID_SP Key from the CyLock Portal. Refer Point #4 in Prerequisites Section.
- Enter Authorization Key: Get the API Key from the CyLock Portal. Refer Point #4 in Prerequisites Section.
- Enter Radius Secret: This Radius secret key is used to communicate between the firewall and the RADIUS Proxy server
- Enter AD / LDAP Admin Secret: Enter Your AD / LDAP Admin Password.
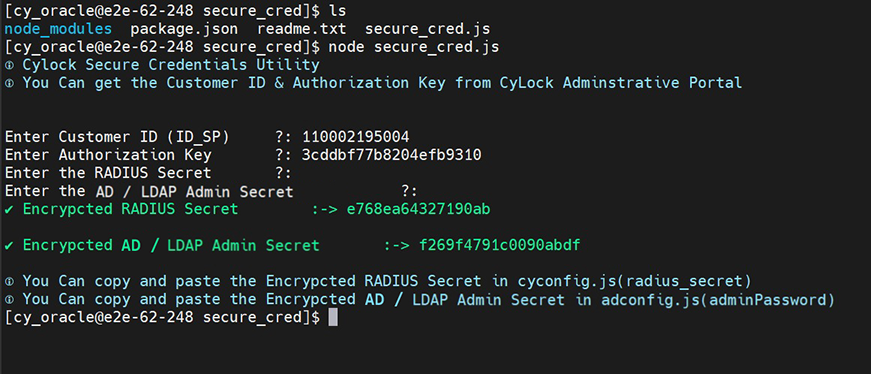
Figure 2 – Encrypting RADIUS Secret and AD / LDAP Password
Copy and paste the Encrypted RADIUS Secret into the “radius_secret” field in cyconfig.js file.
Copy and paste the Encrypted AD / LDAP Admin Secret into the “password" field in adconfig.js file.
Note:The RADIUS Secret and AD / LDAP Password should always be encrypted.
Starting CyLock MFA RADIUS Proxy
Manual Start (Windows and Linux):
- Open terminal window
- Go to the folder where CyLock MFA RADIUS proxy component was copied
- Execute the command “node radius.js”
Auto Start (Linux):
To start the component automatically create and run as service
For creating service file follow the below steps:
- Open terminal window
- Execute
vi/etc/systemd/system/cylockradiusservice.service
- Copy and paste the below contents from start of the file to end of the file in cylock radius service file.
//*****Start of the file*****
[Unit]
Description=cylockradiusservice
After=syslog.target
After=network.target[Service]
User=cylock_iam
//Replace with your system user name
Type=simple
[Service]
Restart=always
StandardOutput=syslog
StandardError=syslog
//Provide the path of the CyLock MFA
RADIUS proxy component (server.js)
WorkingDirectory=/home/cylock_iam/package/
//Provide the path of the CyLock MFA
RADIUS proxy component (server.js)
ExecStart=/usr/bin/node /home/cylock_iam/package/server.js
SyslogIdentifier=cylockradiusservice
[Install]
1.WantedBy=multi-user.target
//******End of the file******
- 4.Save and exit vi editor by entering the following command
a.:wq!
- 5.Enable the service by entering the following command
a.systemctl enable cylockradiusservice.service
- 6.Start the service by entering the following command.
a.systemctl start cylockradiusservice.service
Note:For Windows OS, create a service for the batch file (.bat) using nssm.exe utility and start the service.
Configuring Array AG Device Settings
CyLock MFA integrates with your Array AG Series device-based VPN via RADIUS to add Multi-Factor Authentication (MFA) to SSL VPN login. In this context your Array AG Series device will act as RADIUS client and the CyLock MFA RADIUS Proxy component as the RADIUS server.
Configuring the Array AG Device for RADIUS Authentication
1.Open Array AG Admin Console on Your Browser.
Ex: https://54.175.58.xx:8888
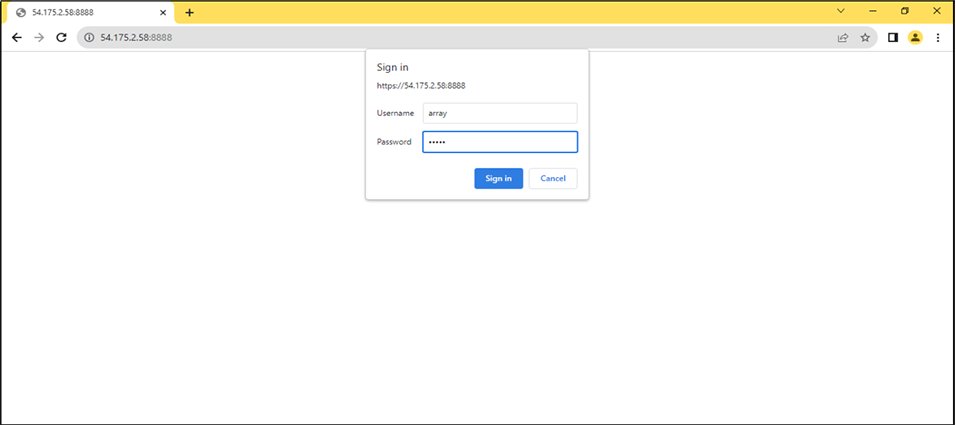
Figure 3 – Array AG Admin Console Login
2.Select Mode as Config > Select Virtual Site Home > Choose Your Respective site name (vpn_site).
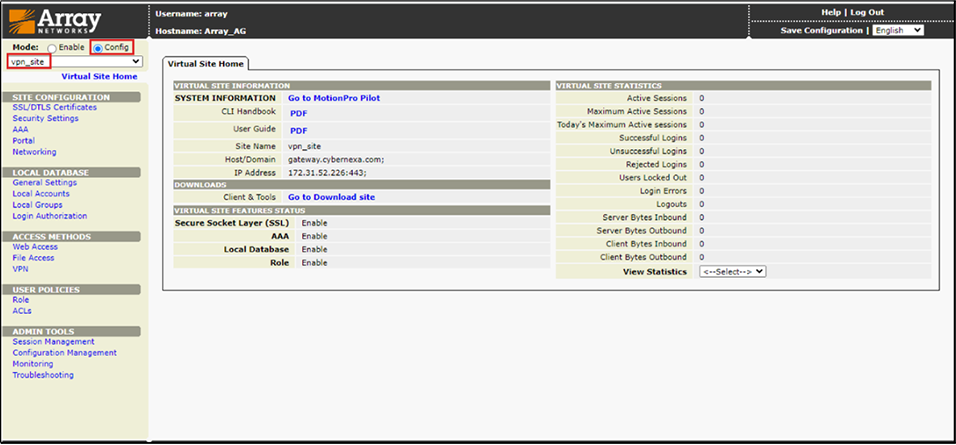
Figure 4 – Virtual Site Home page
3.In the “Site Configuration” section, navigate to “AAA”. In General, select the Enable AAA checkbox as shown in below Figure 5.
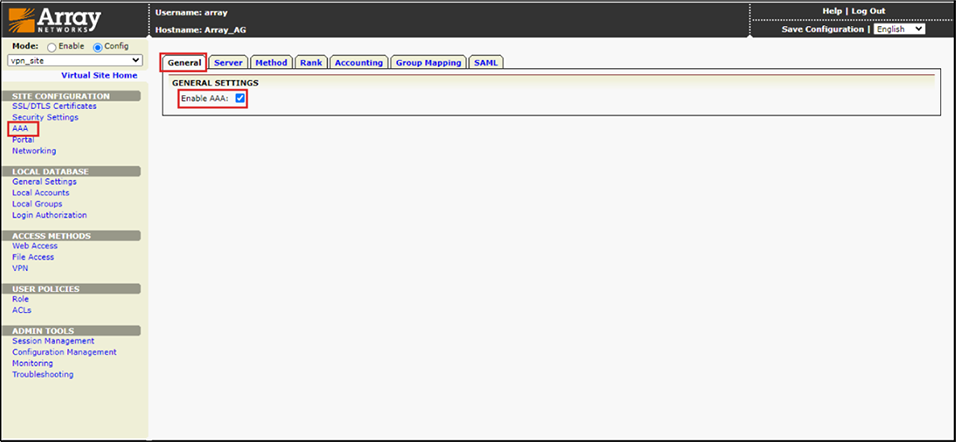
Figure 5 – Configuring General Settings
4. In AAA Site Configuration, go to “Server” and select “RADIUS”, then click the “Add” button to configure the RADIUS.
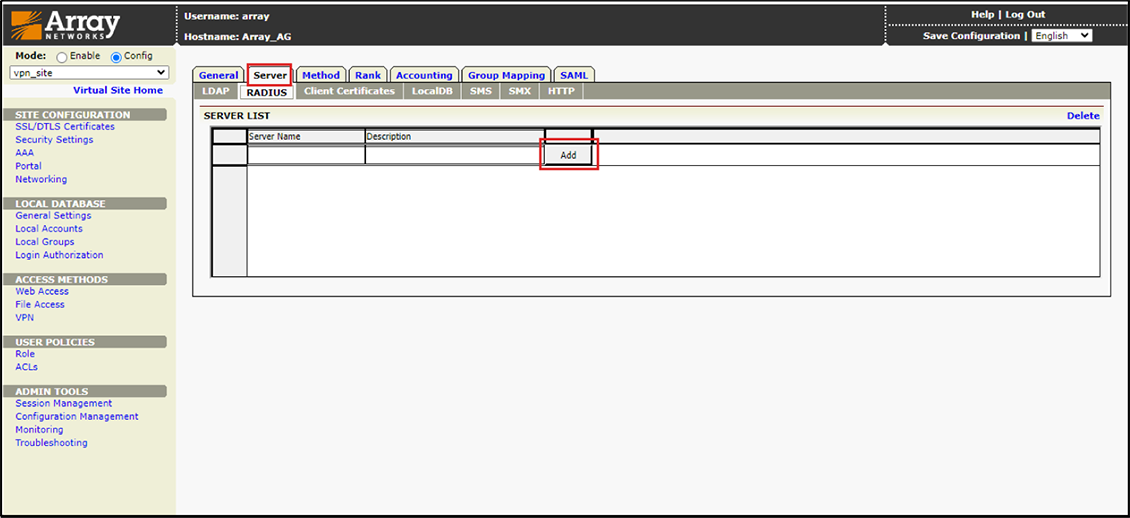
Figure 6 – Adding Server List
5.Server Name: Enter a friendly name for the RADIUS Server (Ex: CyLock RADIUS).
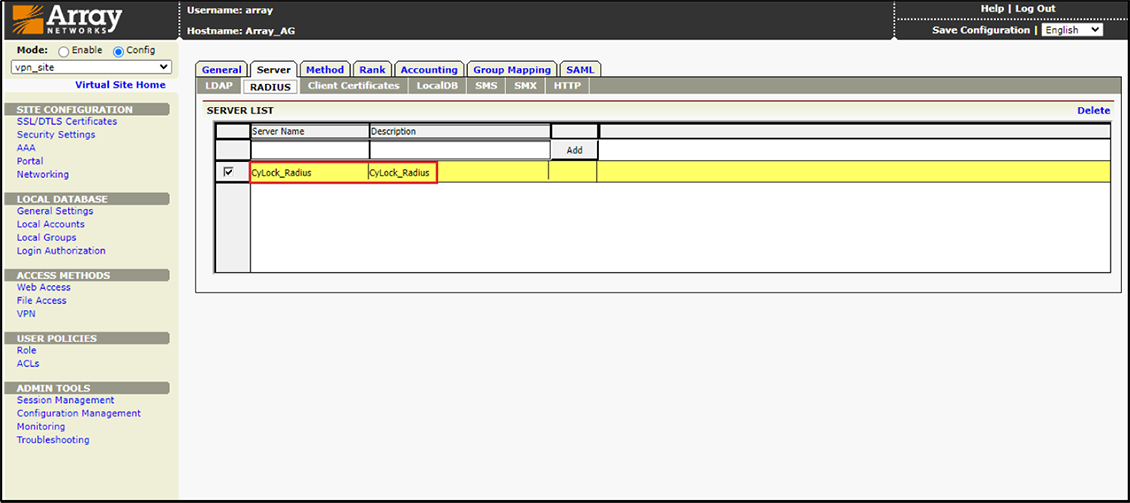
Figure 7 – Entering Name for Radius
6.Once added, double-click the “CyLock_Radius” Server Name.
Figure 8 – Clicking the CyLock Radius
7.Click on “Add RADIUS Server” to configure Radius Server Details.
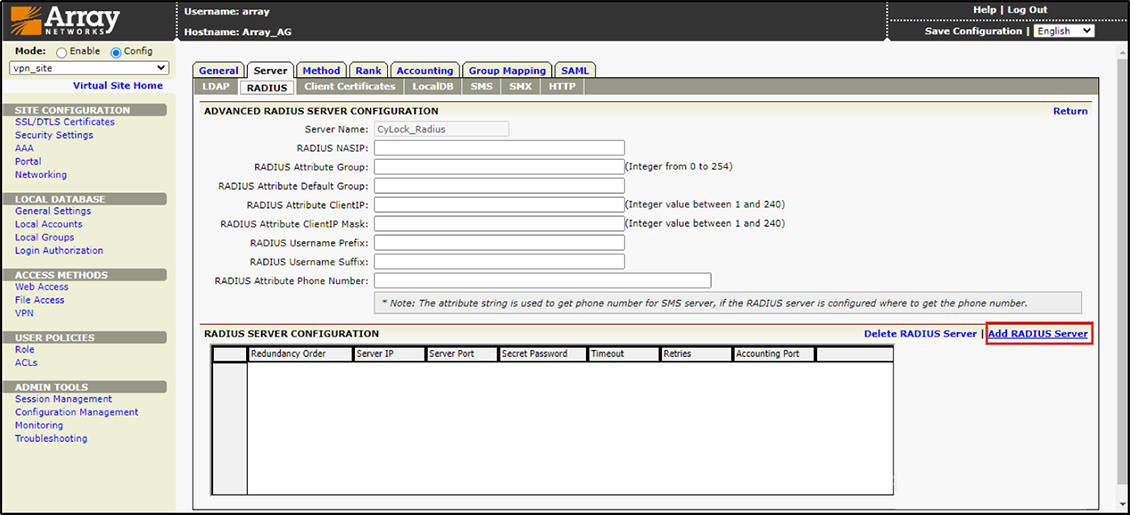
Figure 9 – Clicking on Add Radius Server
8.In the Radius Server profile dialog, enter the configuration details for your RADIUS.
Server IP: Enter Radius Server IP Address
Server Port:Enter the Default Radius Server Port
Secret Password:Enter Plain Secret Key. The string used to authenticate the Array AG Device to the RADIUS Server.
Timeout:120 seconds
Redundancy Order:1
Retries:1
After Entered the Radius Server details, click Save.
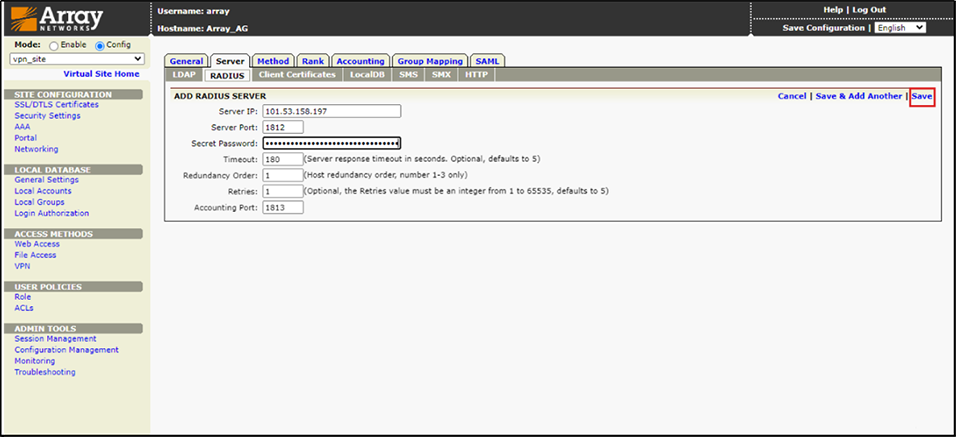
Figure 10 – Entering Radius Server Details
9.After the configuration has been saved then Click “Save Configuration” to Apply Changes.
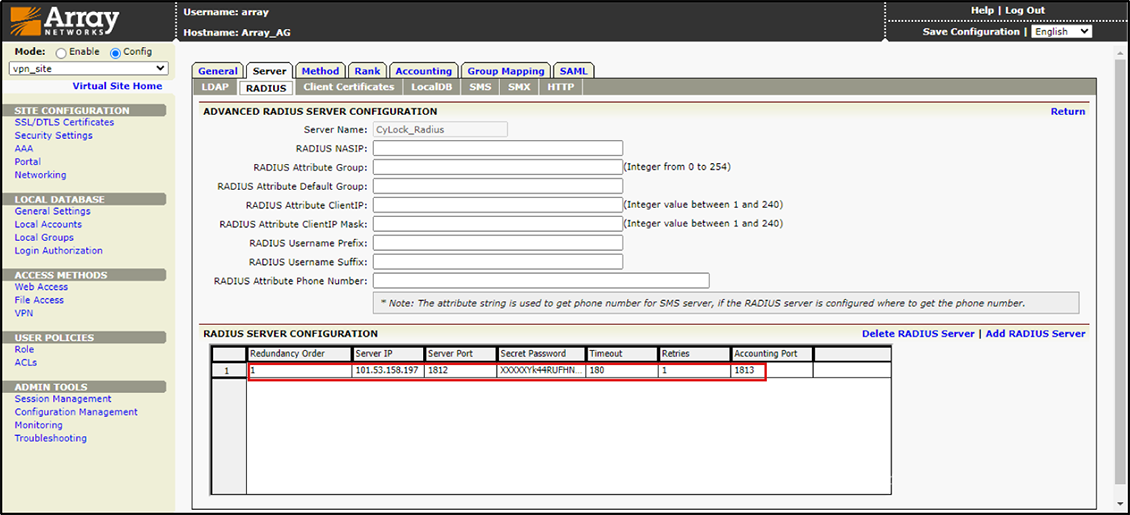
Figure 11 – Applying Changes
10.In the Site Configuration Section, navigate to “AAA”, then “Method”, and click Add Method.
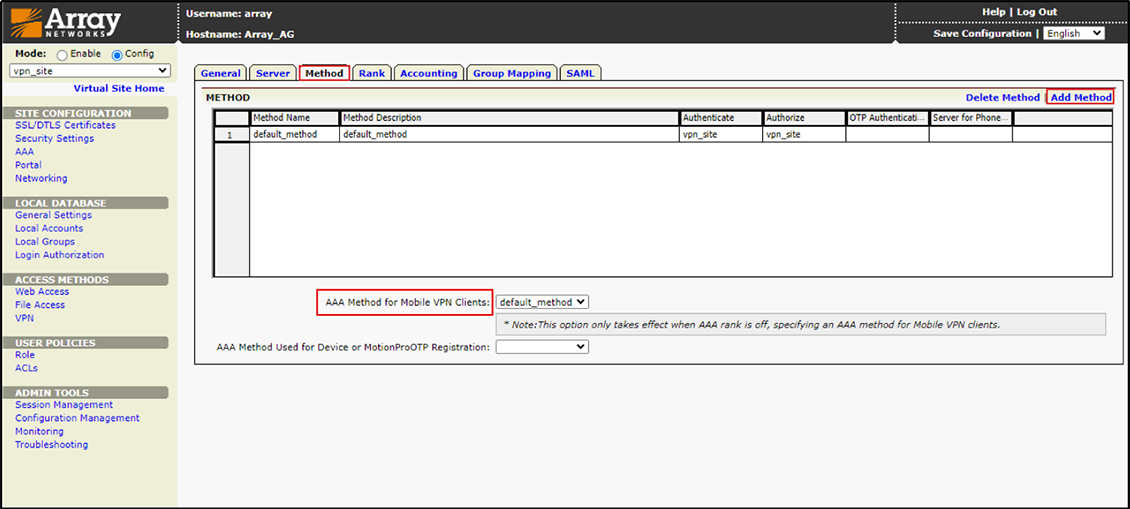
Figure 12 – Adding Authentication Method
11.Enter “CyLock” as the method's name and Choose “CyLock RADIUS” as the authentication method, then click the Save button.
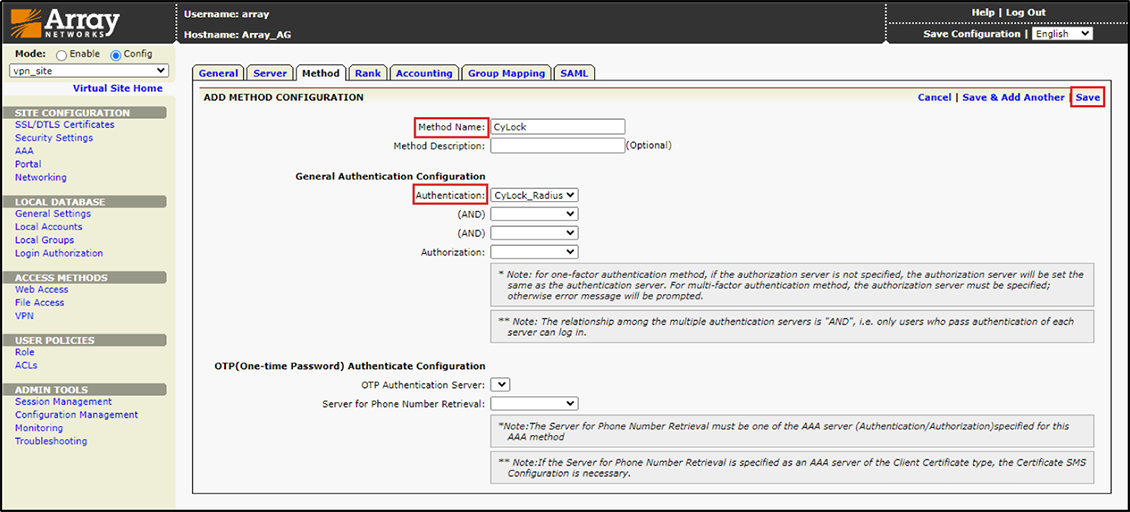
Figure 13 – Choosing Method Name as CyLock RADIUS
12.Whether after adding the method. Select “CyLock” as the AAA mechanism for your mobile VPN client, and then click Apply Changes.
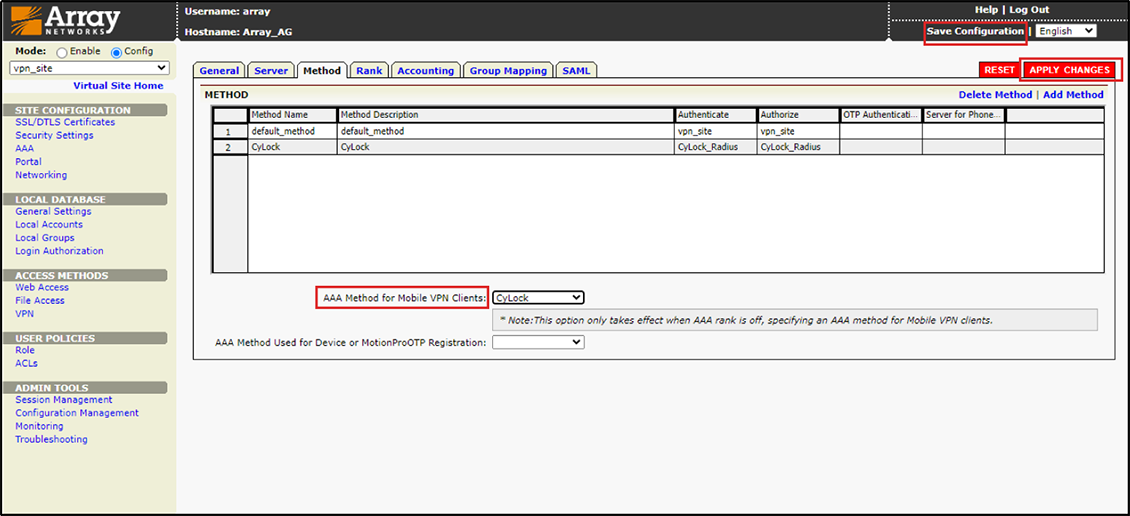
Figure 14 – Applying Changes
13. Adding CyLock Theme for CyLock MFA Authentication Methods.
In Site Configuration > Go to Portal > Themes > Import Theme.
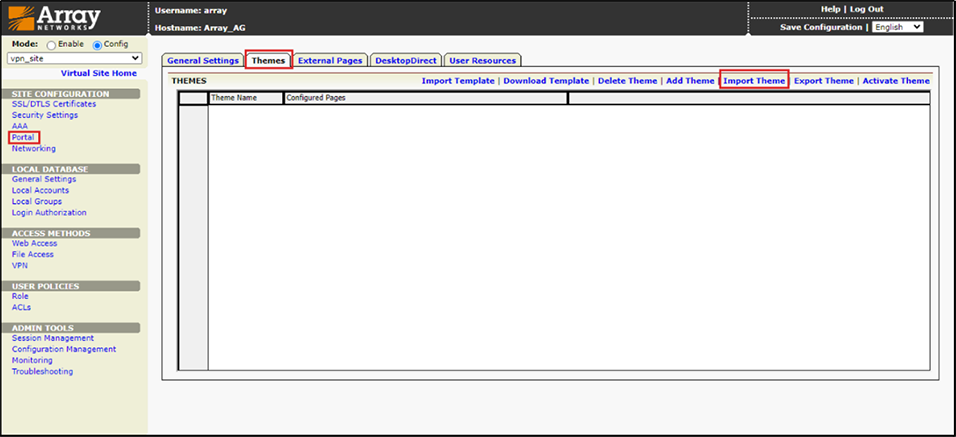
Figure 15 – Adding CyLock Theme
14.Choose the CyLock theme, then check the "Enable Rewrite" box. Download the CyLock_theme from the CyLock Portal. Refer to point #7 in the Prerequisites section.
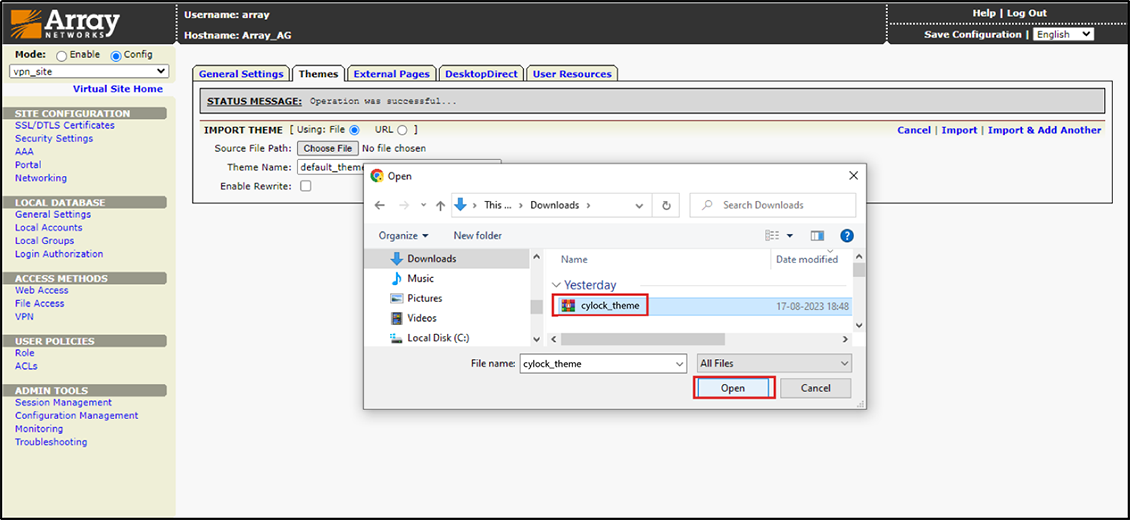
Figure 16 – Choosing CyLock Theme
15.Enter CyLock as the Theme Name, then click ‘Import’.
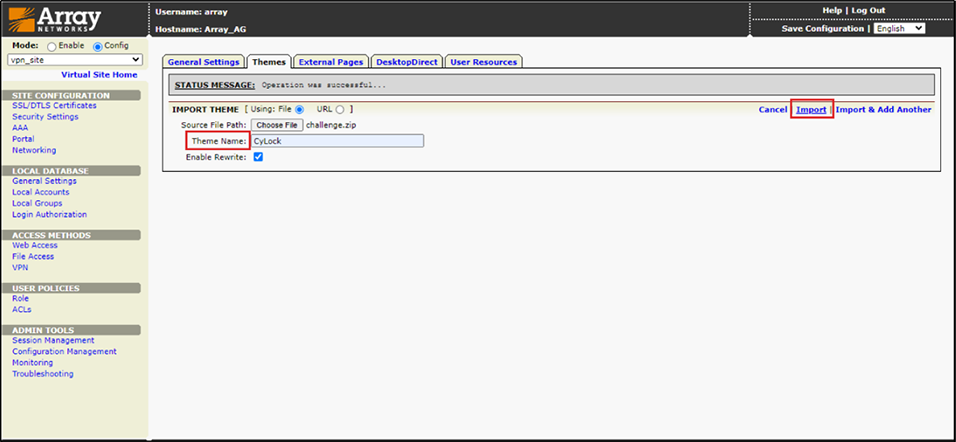
Figure 17 – Entering name for Theme
16.After importing the CyLock theme, choose the Imported CyLock theme, click “Activate Theme”, and then Save Configuration.
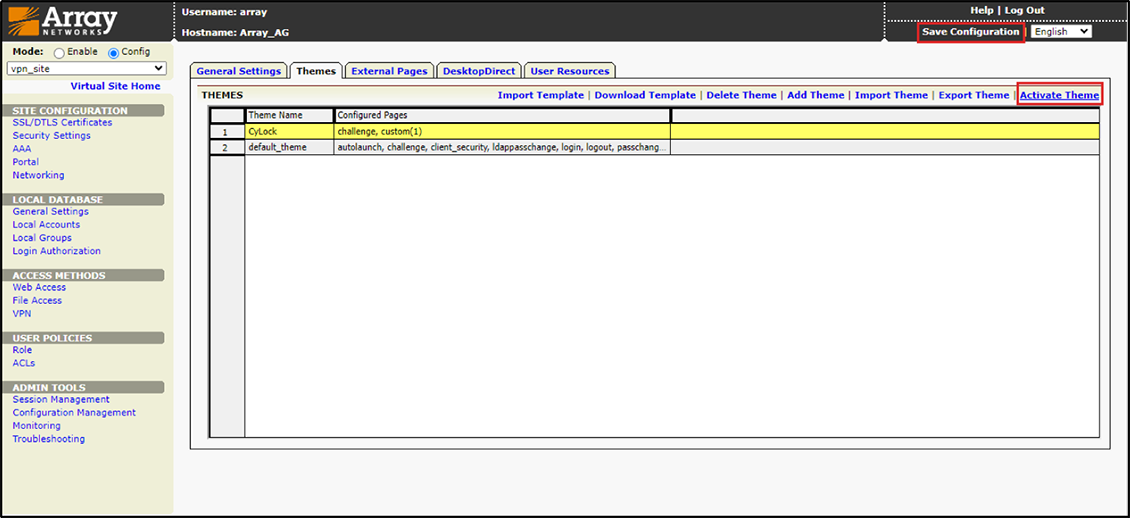
Figure 18 – Activating the CyLock Theme
Test your setup
Types of Authentication Options:
CyLock allows the following Authentications during SSL VPN Login.
| # |
Mode |
Process Step |
| 1 |
Default Mode |
In password field enter << Your password >> (for carrying out the default authentication) |
| 2 |
Online (Push) |
In password field enter << Your password >>,1 (for carrying Online MFA Push authentication) |
| 3 |
Online (Push + PIN) |
In password field enter << Your password >>,2 (for carrying Online MFA Push+PIN authentication) |
| 4 |
Online (Push + Bio) |
In password field enter << Your password >>,3 (for carrying Online MFA Push+Bio authentication) |
| 5 |
Offline (CR-OTP - Display) |
In password field enter << Your password >>,4 (for carrying Offline MFA CR-OTP (Display) authentication) |
| 6 |
Offline (CR-OTP – Email) |
In password field enter << Your password >>,5 (for carrying out Offline MFA CR-OTP (Email) authentication) |
| 7 |
Offline (CR-OTP – SMS) |
In password field enter << Your password >>,6 (for carrying Offline MFA CR-OTP (SMS) authentication) |
| 8 |
Offline (POTP - Email) |
In password field enter << Your password >>,7 (for carrying out Offline MFA POTP (Email) authentication) |
| 9 |
Offline (POTP – SMS) |
In password field enter << Your password >>,8 (for carrying Offline MFA POTP (SMS) authentication) |
| 10 |
Offline (TOTP) |
In password field enter << Your password >>,9 (for carrying Offline MFA TOTP authentication) |
| 11 |
Offline (Grid) |
In password field enter << Your password >>,10 (for carrying Offline MFA Grid authentication) |
| 12 |
Online (QR - Push) |
In password field enter << Your password >>,11 (for carrying Online MFA QR Push authentication) |
| 13 |
Online (QR – Push + PIN) |
In password field enter << Your password >>,12 (for carrying Online MFA QR Push + PIN authentication) |
| 14 |
Online (QR – Push + Bio) |
In password field enter << Your password >>,13 (for carrying Online MFA QR Push + Bio authentication) |
By using the above authentication mode, we can test SSL VPN Connection.
Test the connection:
(a).Enter the Gateway URL in Browser
Figure 19 – Array AG Gateway Login Page
(b).A push notification or any preferred authentication request is sent to your mobile device as shown in the below Figure 20.
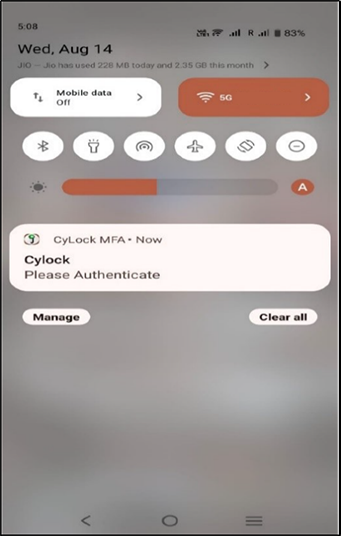
Figure 20 – Push Notification Request
(c).Kindly accept the push request using CyLock MFA Mobile App. After the authentication is approved, the connection will be established.
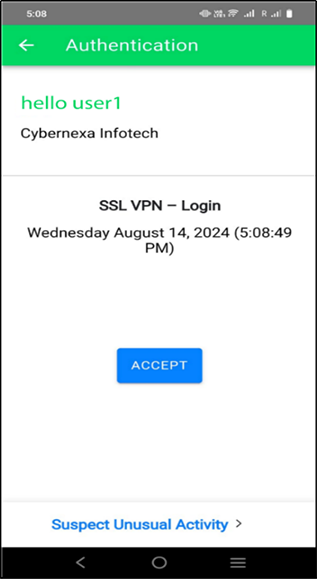
Figure 21 – Accepting the Push Request
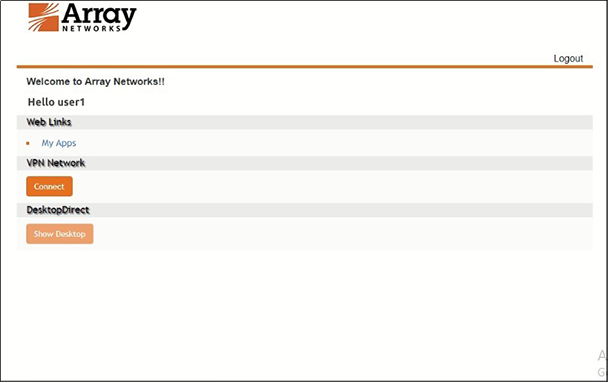
Figure 22 – VPN Connection Established
























