 |
|

 |
|

CyLock MFA enables strong Multi-Factor Authentication for any firewall based SSL VPN user login. CyLock MFA integrates with the firewall through CyLock MFA RADIUS proxy component installed in a server within the organization’s local network.
The CyLock MFA RADIUS proxy component enables any firewall with RADIUS protocol support to carry out a strong Multi-Factor Authentication (MFA) during remote login to remote network through SSL VPN.
Firewall Devices: Cisco ASA Series, Cisco Firepower Next-Generation Firewall (NGFW) series, Cisco Firepower 1000 Series, Cisco ASA 5500-X Series, Cisco PIX Firewall support RADIUS authentication.
CyLock MFA RADIUS proxy component needs to be installed within your network to enable MFA during SSL VPN login process. First factor (user login credentials) can be authenticated with an on-premise AD / LDAP / LDAP Server or against CyLock MFA local store. A typical deployment architecture and process is shown below.
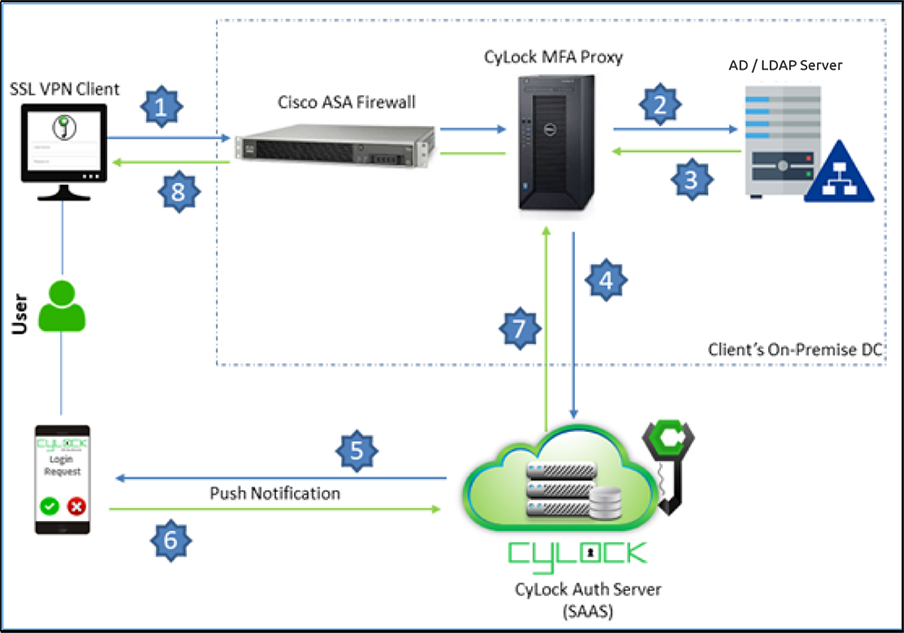
Figure 1 – Deployment Architecture Block diagram of integrating Fortinet Firewall with CyLock RADIUS Proxy
Note:
CyLock MFA RADIUS Proxy component will receive incoming RADIUS requests from your firewall during SSL VPN login. The proxy component will then perform the primary authentication (first factor authentication) either with your internal AD / LDAP / LDAP server or CyLock MFA local store, and then contact CyLock MFA Auth server for second factor authentication.
CyLock MFA RADIUS Proxy can be installed on a physical or virtual host within your network. We recommend a system with at least 4 vCPU, 200 MB disk space, and 4 GB RAM. CyLock MFA RADIUS Proxy supports the following operating systems:
Install Node.JS in the server where the CyLock MFA RADIUS Proxy component will be installed.
Download the CyLock MFA RADIUS Proxy component. Refer Prerequisites section above. After downloading, copy/move the Proxy Component to the respective server.
Go to the folder where the Proxy component has been copied. Extract the CyLock_radius_proxy.zip. After extracting, follow the below steps to configure the component.
On Windows or Linux machine go to the respective folder where the proxy component was copied & extracted.
Open the cyconfig.js file in CyRadius Folder with administrative privileges and change the following properties:
| # | Property Name (key) | Description (value) |
|---|---|---|
| 1 | url |
Enter Auth URL (Ex - https://demoauth.cybernexa.com/api/v2/srv/) Contact the CyLock Support Team to get the Auth Server URL. |
| 2 | id_sp | Customer ID value. Refer point #4 in Prerequisites section. |
| 3 | Authorization | API Key value. Refer point #4 in Prerequisites section. |
| 4 | radius_secret | Paste the Encrypted Radius secret key. To obtain the encrypted RADIUS Secret key, please refer to the Key Encryption Process Section listed below. |
Note: Do not modify the key in the key-value pair.
To enable RADIUS Proxy component, communicate with MS AD / LDAP server or LDAP server, configure the adconfig.js file.
Open the adconfig.js file in CyRadius Folder with administrative privileges and change the below properties.
| # | Property Name (key) | Description (value) |
|---|---|---|
| 1 | Open_ldap_server | Enter your open ldap server URL (ex: ldaps://ldap.cybernexa.com) |
| 2 | domain | Provide your AD / LDAP domain name. |
| 3 | url | For secured LDAP: ldaps://computername.domain.com or else simply use For normal LDAP: ldap://computername.domain.com |
| 4 | baseDN | Domain name |
| 5 | Password | Paste Your AD / LDAP server Administrator user’s Encrypted password. To obtain the encrypted AD / LDAP Password, please refer to the Key Encryption Process Section listed below. |
Note: Do not modify the key in the key-value pair.
Encrypting Radius Secret Key and AD / LDAP Password.
a. After Unzip the radius_proxy.zip file. Go to the secure_cred directory and execute the "secure_cred.js" file using the command below
(i).node secure_cred.js
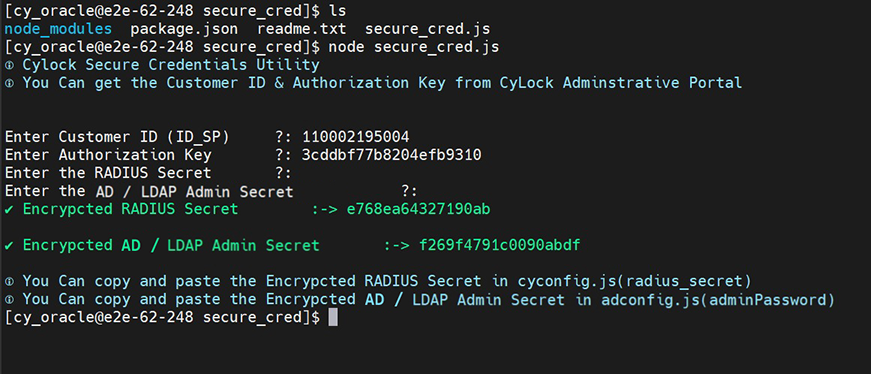
FFigure 2 – Encrypting RADIUS Secret and AD / LDAP Password
Copy and paste the Encrypted RADIUS Secret into the “radius_secret” field in cyconfig.js file.
Copy and paste the Encrypted AD / LDAP Admin Secret into the “password" filed in adconfig.js file.
Note:The RADIUS Secret and AD / LDAP Password should always be encrypted.
To start the component automatically create and run as service
For creating service file follow the below steps:
//*****Start of the file*****
[Unit]
Description=cylockradiusservice
After=syslog.target
After=network.target[Service]
User=cylock_iam
//Replace with your system user name
Type=simple
[Service]
Restart=always
StandardOutput=syslog
StandardError=syslog
//Provide the path of the CyLock MFA RADIUS proxy component (server.js) WorkingDirectory=/home/cylock_iam/CyRadius/
//Provide the path of the CyLock MFA RADIUS proxy component (server.js)
ExecStart=/usr/bin/node /home/cylock_iam/CyRadius/server.js
SyslogIdentifier=cylockradiusservice
[Install]
1.WantedBy=multi-user.target
//******End of the file******
a.:wq!
a.systemctl enable cylockradiusservice.service
a.systemctl start cylockradiusservice.service
Note:For Windows OS, create a service for the batch file (.bat) using nssm.exe utility and start the service.
CyLock MFA integrates with your firewall device based VPN via RADIUS to add Multi-Factor Authentication (MFA) to SSL VPN login. In this context your firewall device will act as RADIUS client and the CyLock MFA RADIUS Proxy component as the RADIUS server.
The Add AAA Server Group dialog displays.
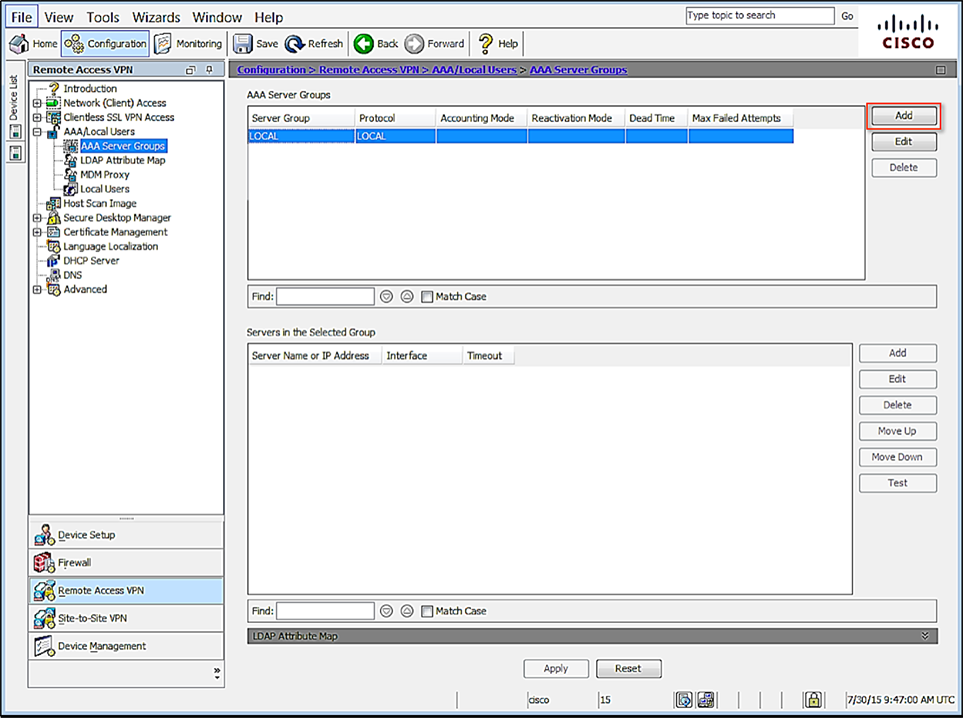
Figure 3 – Adding AAA Server Group
AAA Server Group – specify a name to identify the group for the MFA server
Protocol - select RADIUS if necessary
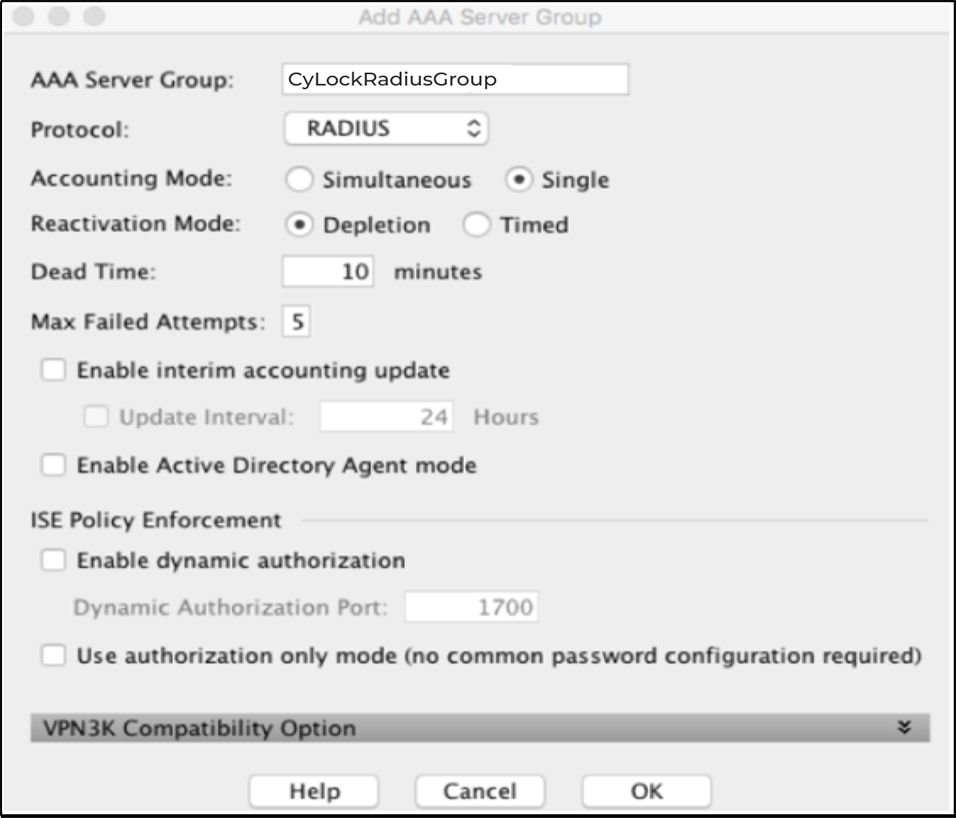
Figure 4 – Configuring AAA Server Group
Select the server group just created.
The Edit 'Server Name' Server dialog displays.
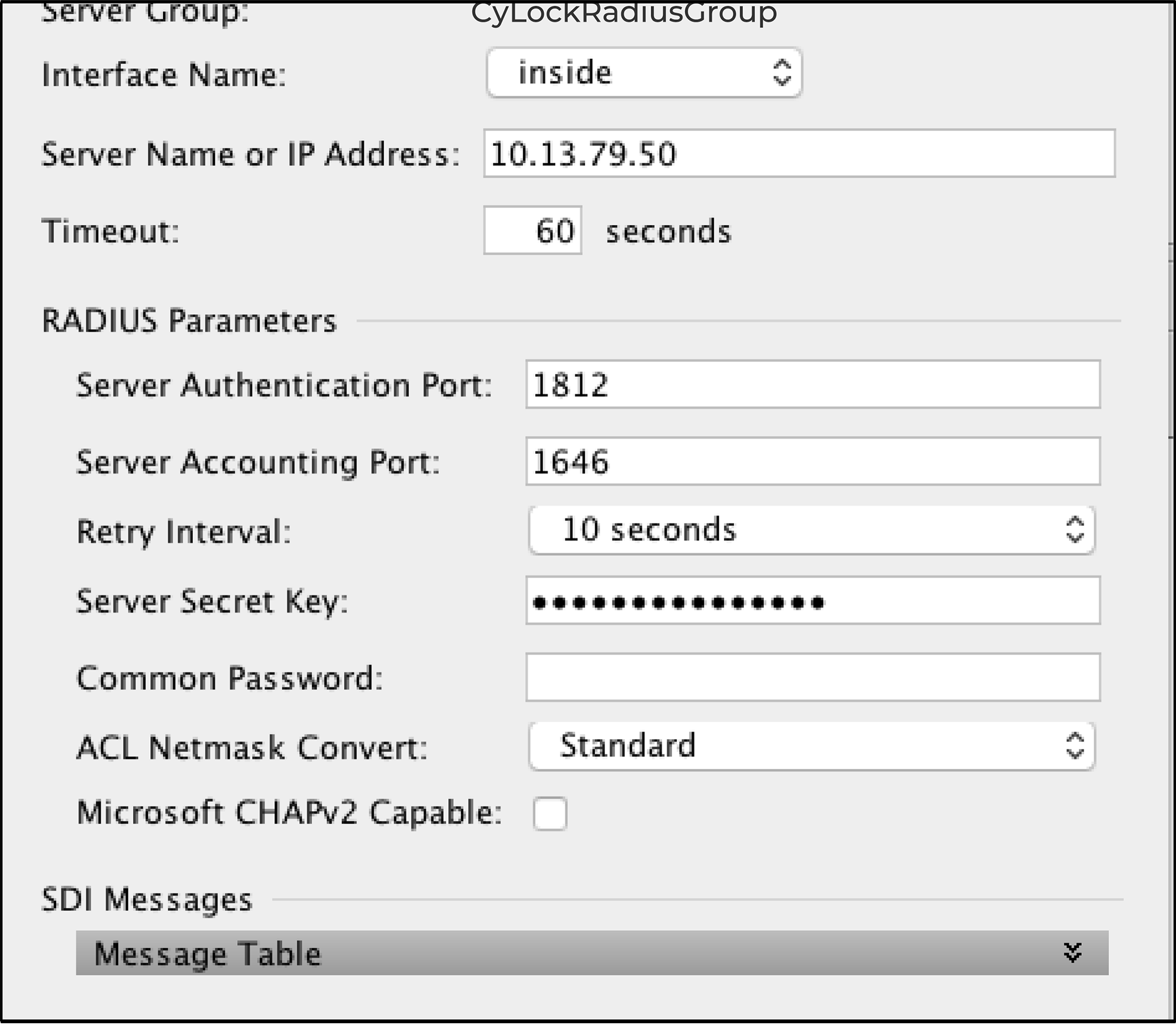
Figure 5 – Entering RADIUS Server Details
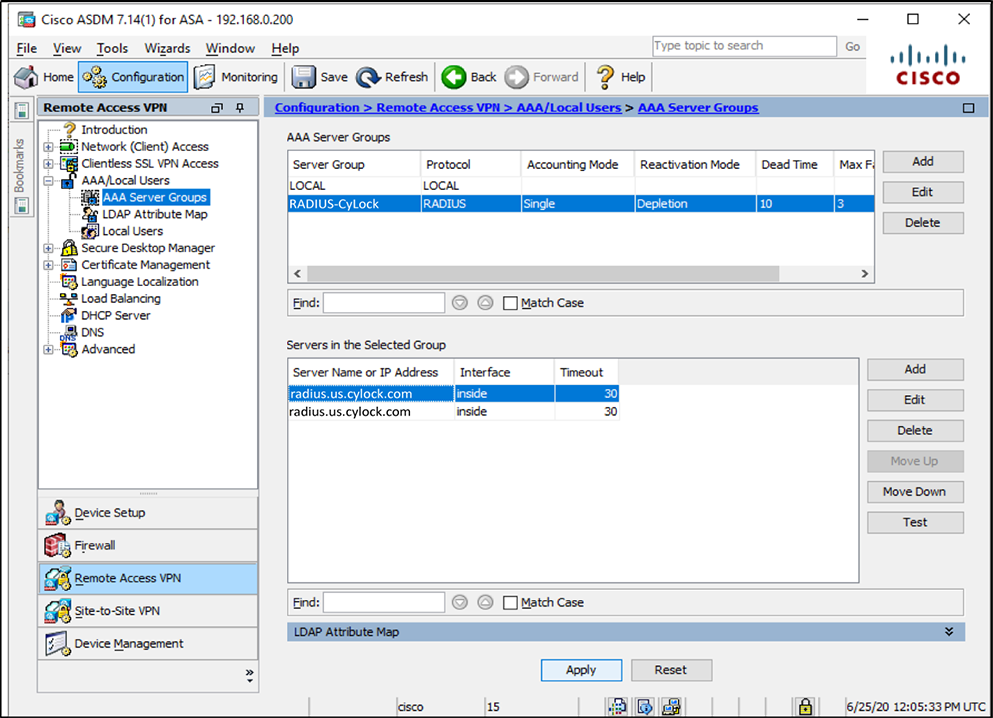
Figure 6 – Clicking Apply Button to save changes
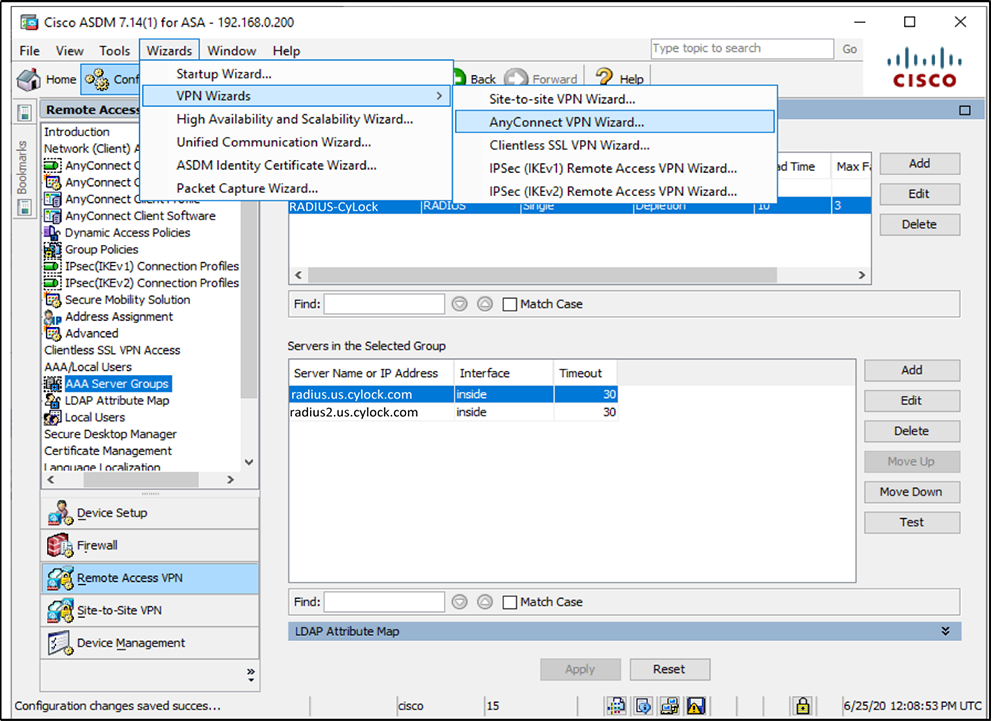
Figure 7 – Configuring AnyConnect VPN Wizard
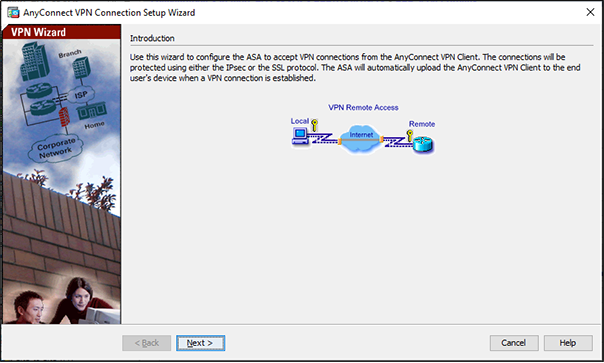
Figure 8 – Clicking Next
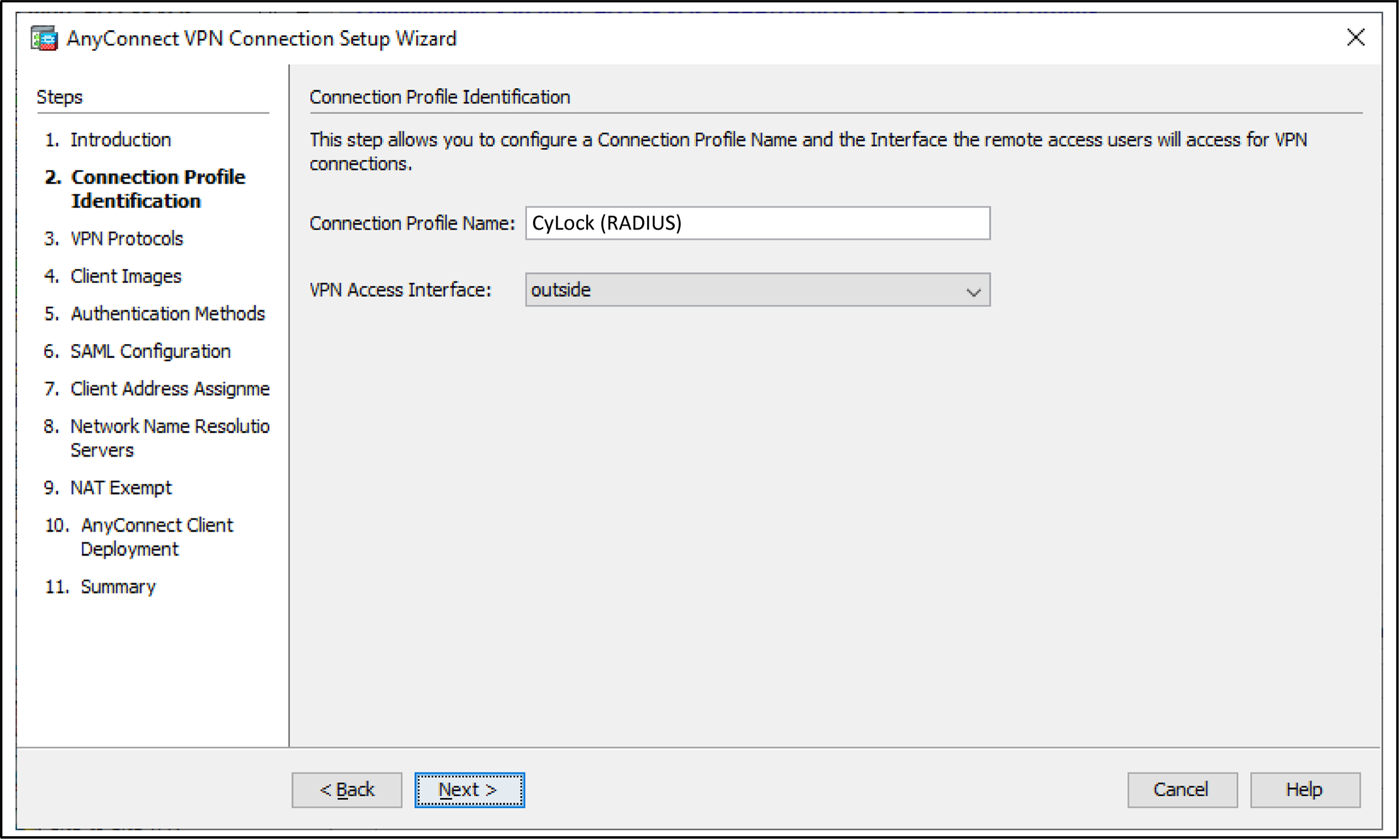
Figure 9 – Entering Connection Profile Name
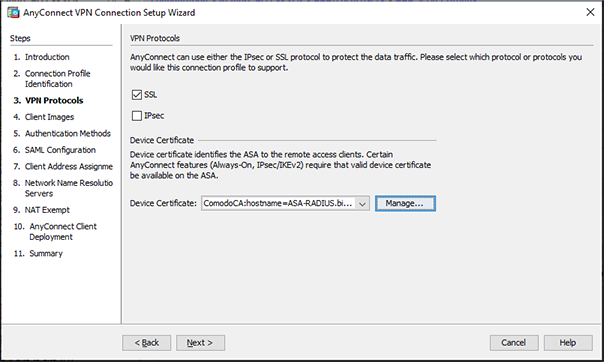
Figure 10 – Selecting SSL and Choosing Device Certificate
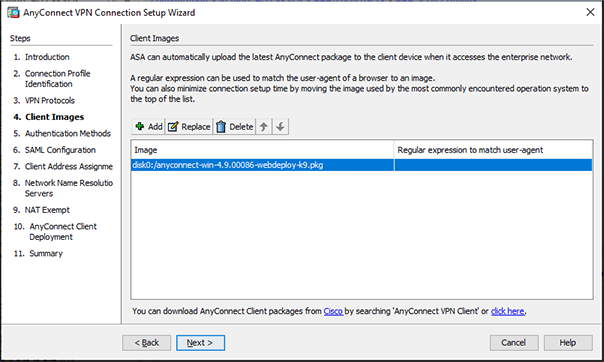
Figure 11 – Choosing Client Image
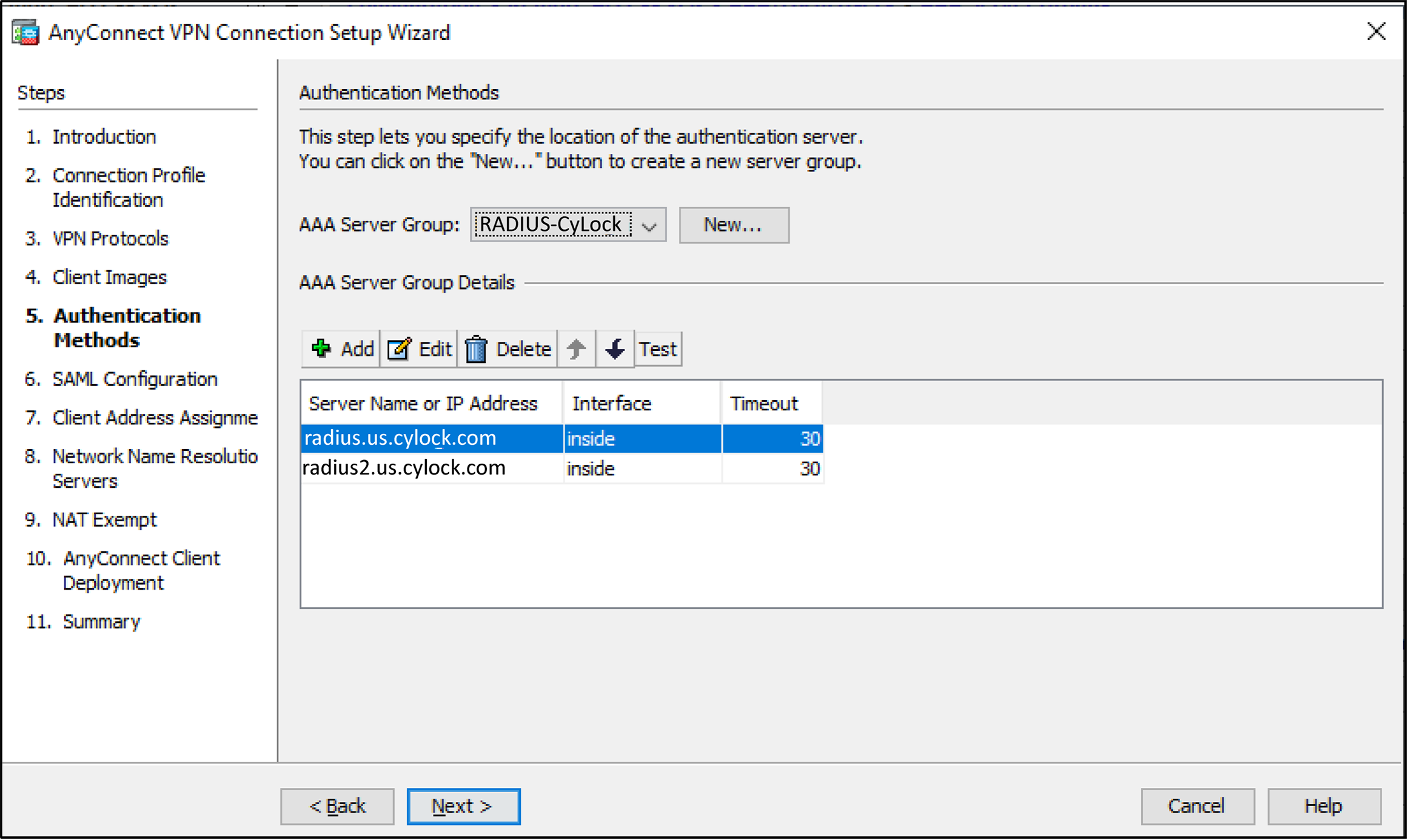
Figure 12 – Choosing AAA Server Group
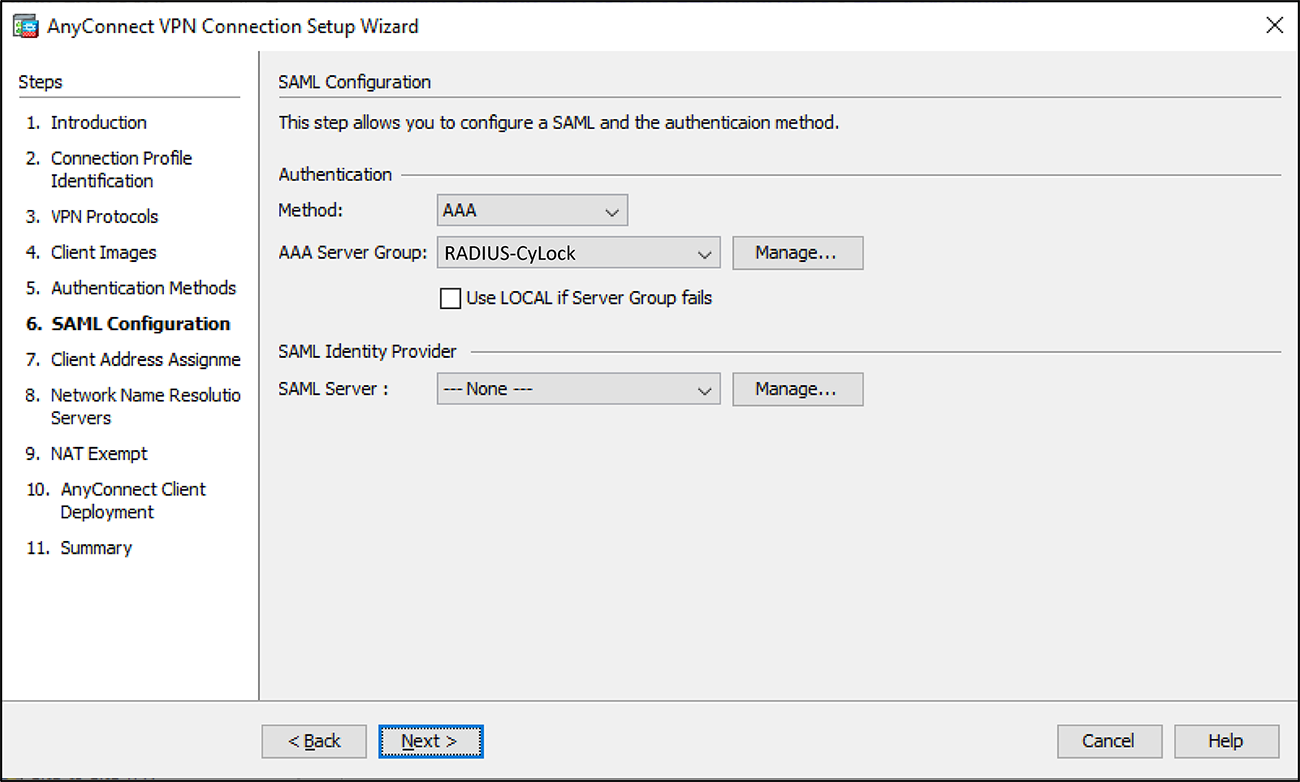
Figure 13 – Clicking Next
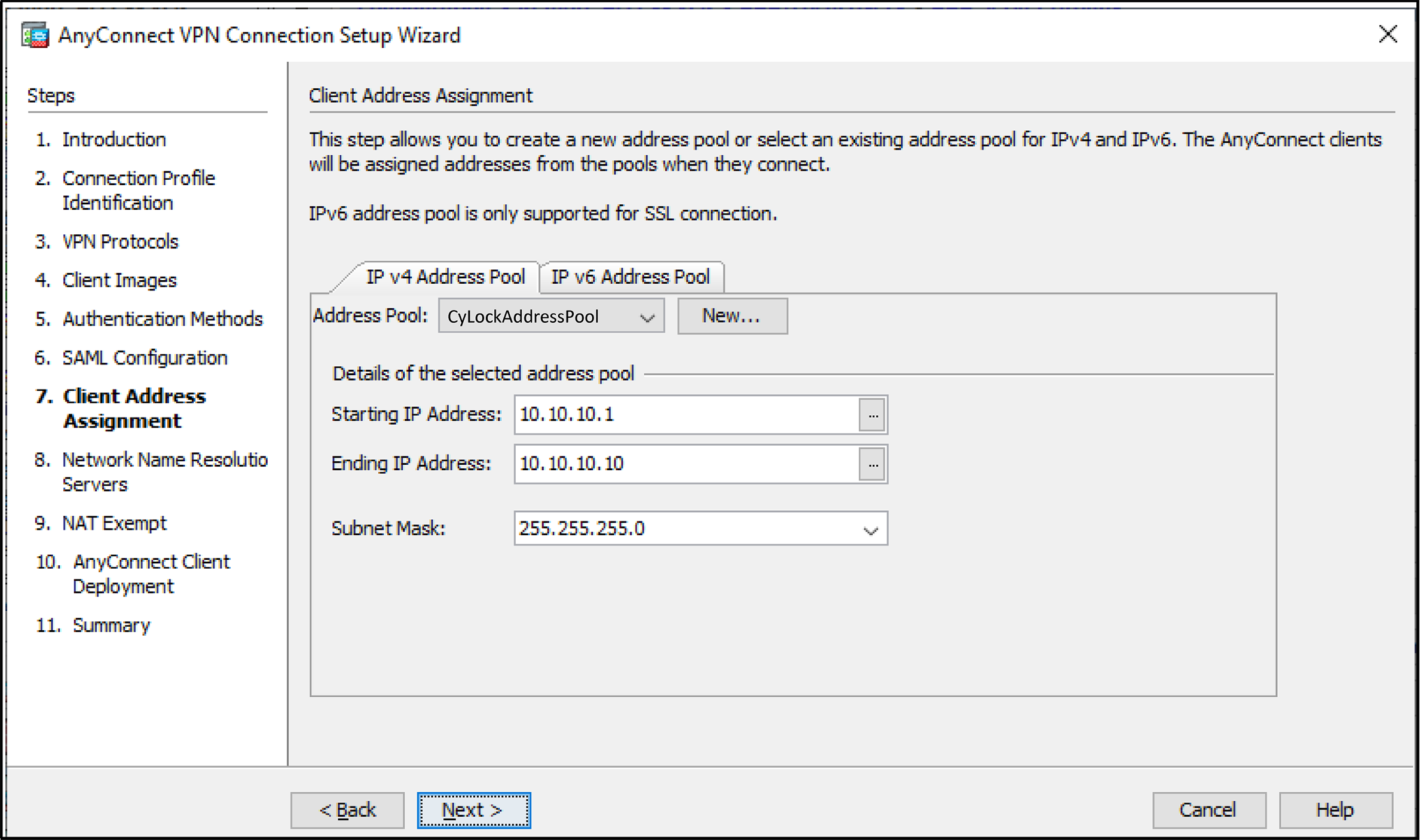
Figure 14 – Selecting Address Pool
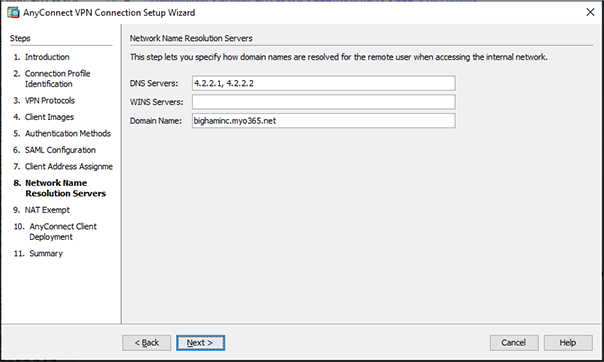
Figure 15 – Configuring DNS Settings
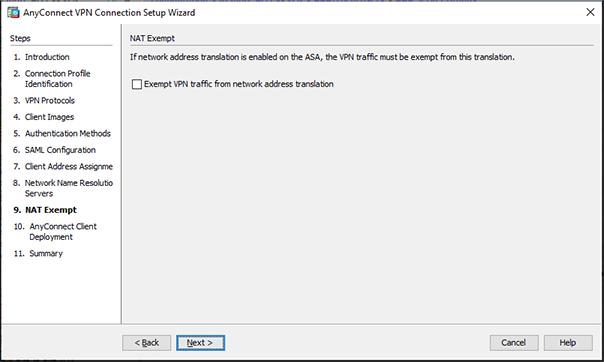
Figure 16 – Unselecting the NAT Exempt

Figure 17 – Clicking Next
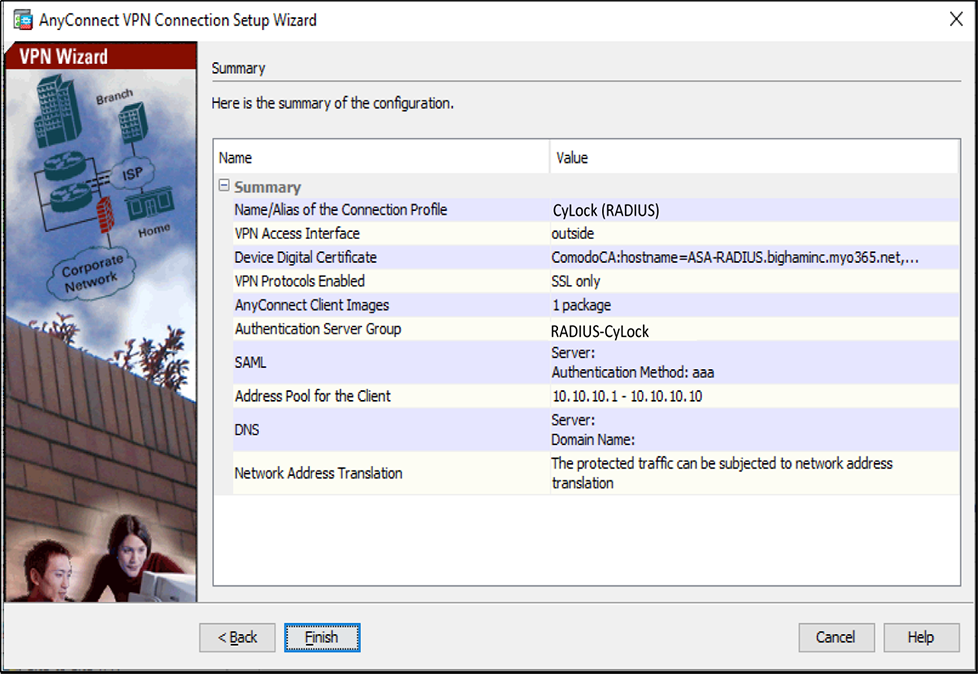
Figure 18 – Validating the Settings
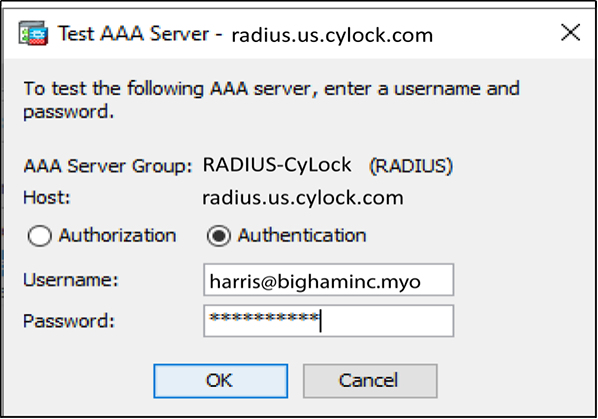
Figure 19 – ASDM Interface
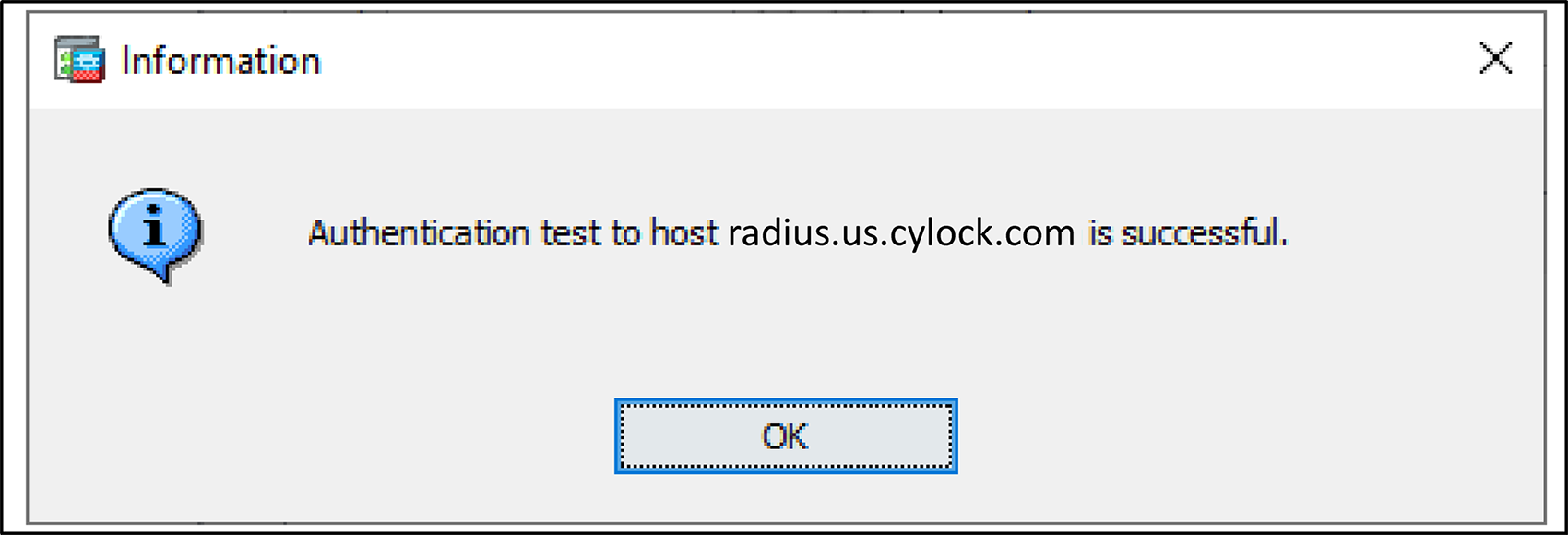
Figure 20 – Testing the Connection
Types of Authentication Options:
1.CyLock allows the following Authentication during SSL VPN Login
| # | Mode | Process Steps |
|---|---|---|
| 1 | Default Mode | In password field enter << Your password >> (for carrying out the default authentication) |
| 2 | Online (Push) | In password field enter << Your password >>,1 (for carrying Online MFA Push authentication) |
| 3 | Online (Push +PIN) | In password field enter << Your password >>,2 (for carrying Online MFA Push+PIN authentication) |
| 4 | Online (Push +Bio) | In password field enter << Your password >>,3 (for carrying Online MFA Push+Bio authentication) |
| 5 | Offline (CR-OTP - Display) | In password field enter << Your password >>,4 (for carrying Offline MFA CR-OTP (Display) authentication) |
| 6 | Offline (CR-OTP – Email) | In password field enter << Your password >>,5 (for carrying out Offline MFA CR-OTP (Email) authentication) |
| 7 | Offline (CR-OTP – SMS) | In password field enter << Your password >>,6 (for carrying Offline MFA CR-OTP (SMS) authentication) |
| 8 | Offline (POTP - Email) | In password field enter << Your password >>,7 (for carrying out Offline MFA POTP (Email) authentication) |
| 9 | Offline (POTP – SMS) | In password field enter << Your password >>,8 (for carrying Offline MFA POTP (SMS) authentication) |
| 10 | Offline (TOTP) | In password field enter << Your password >>,9 (for carrying Offline MFA TOTP authentication) |
2.Test your setup with the Cisco AnyConnect VPN client.
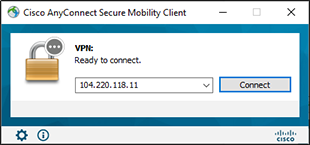
Figure 21 – Cisco AnyConnect VPN Client
3. Enter Your SSL VPN Login Credential and Choose Group > CyLock (RADIUS)
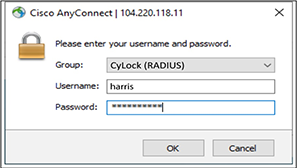
Figure 22 – Entering Login Credentials
4. On successful 1FA, A push notification or any preferred authentication request (2FA) is sent to your mobile device as shown in the below figure 21.
5. Accept the Push + PIN request using CyLock MFA Mobile App. After the authentication is approved, the VPN connection will be established.
6. Enter 6 Digit Pin that you have set during the device registration and then press
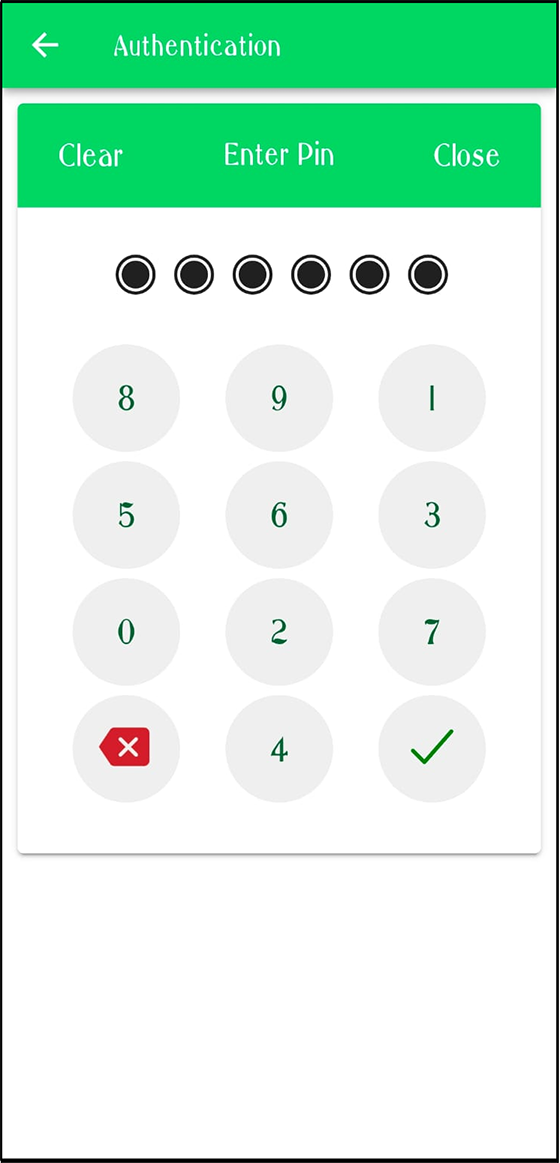
Figure 25 – Entering 6 Digit pin
7. The VPN connection is established after authentication is approved using the CyLock MFA Mobile APP.
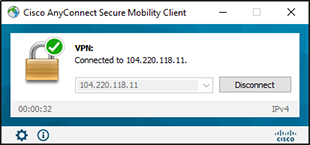
Figure 26 – VPN Connection Established