 |
|

 |
|

Secure Shell (SSH) is a vital protocol used for securely accessing and managing Linux servers remotely by authenticating using a user name and password.
CyLock MFA for Secure Shell (SSH) is a crucial component of modern cybersecurity strategies, offering enhanced security, resilience, and compliance adherence. By implementing MFA for SSH, organizations can effectively mitigate the risks associated with unauthorized access while maintaining operational efficiency and user experience.
CyLock MFAsteps up as a vital solution, demanding users to confirm their identity through multiple distinct methods. This fortifies the login access to Linux Servers, marking an indispensable measure essential for combating the dangers of password compromise, ensuring adherence to industry regulations, and, above all, safeguarding sensitive data.
CyLock PAMmodule can be installed on an Ubuntu Server to quickly enable two factor authentications during SSH login. A typical deployment architecture and process is shown below.
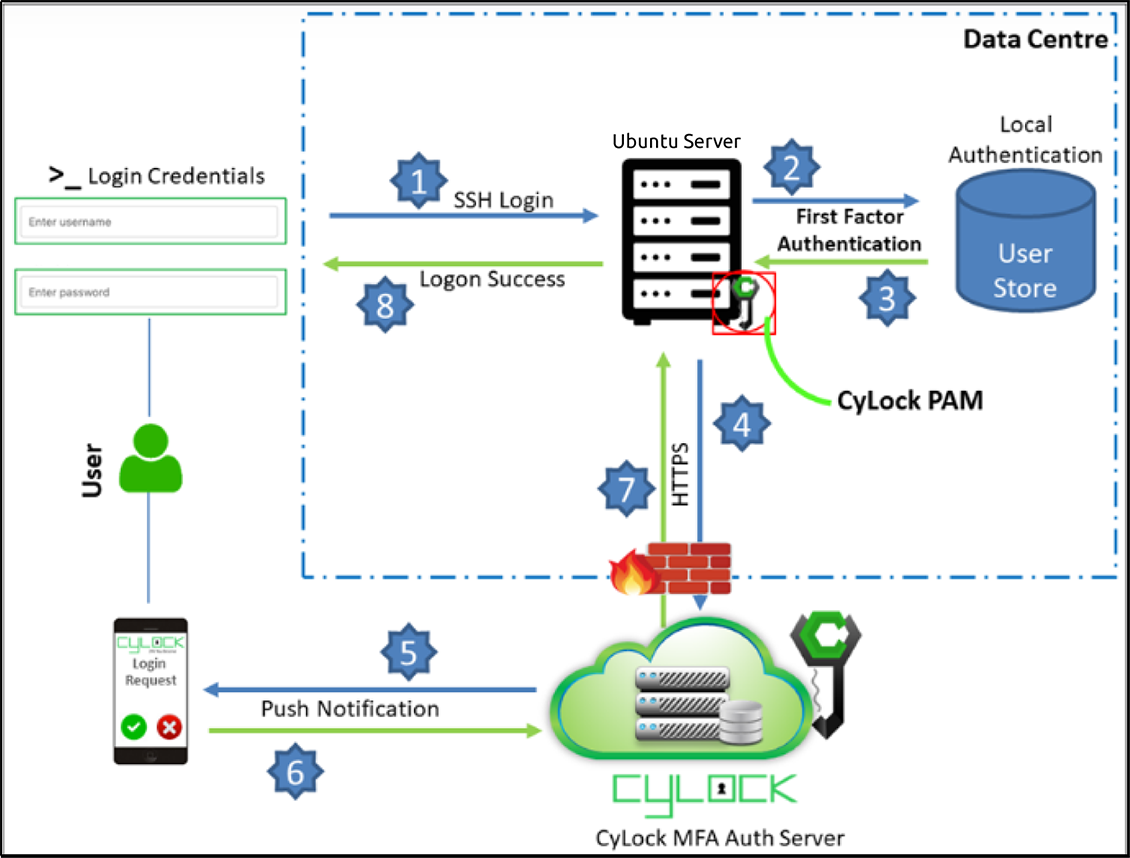
Figure 1: Deployment Architecture and process flow of SSH Login
The CyLock MFA PAM Module can be installed on a Linux Server. We recommend a Server with at least 4 vCPU, 200 MB disk space, and 8 GB RAM.
Supported Linux Distributions:
This document pertains to Ubuntu Linux distribution. Download the CyLock MFA PAM module for Ubuntu and move the same in the respective Server.
cat /etc/os-release
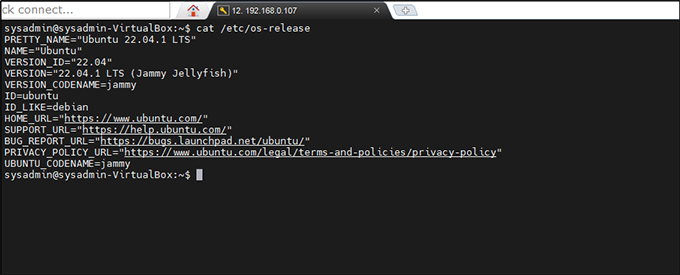
Figure 2: Verifying the Ubuntu OS version
sudo apt-get update
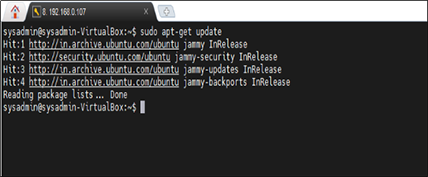
Figure 3: Updating the Package
Here Mobaxterm is used for hosting SSH sessions, In Mobaxterm click on the ‘up arrow’ symbol at left hand side. Refer Figure 4
Figure 4 : Uploading CyLock MFA PAM module into the Ubuntu server
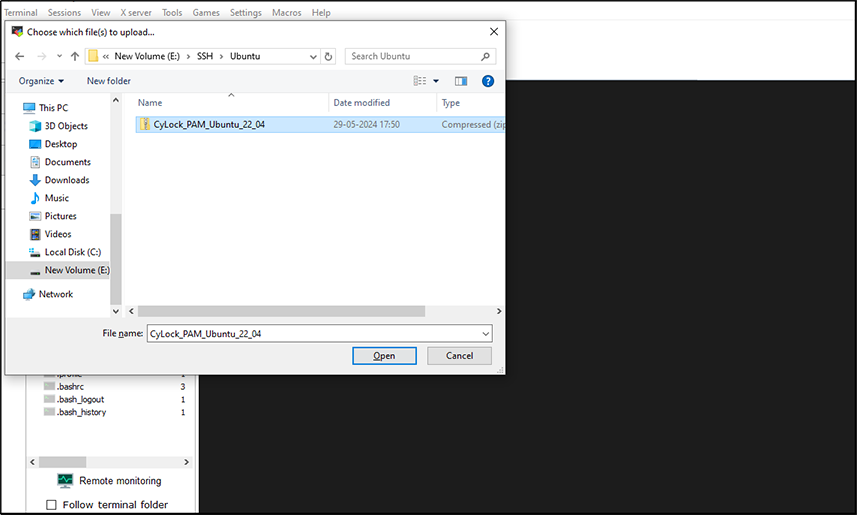
Figure 5: Selecting the downloaded CyLock MFA Ubuntu PAM module from the local machine
sudo unzip CyLock_PAM_RHEL_9_4.zip
After you unzip the file, you can see an unzipped folder. Refer Figure 6.
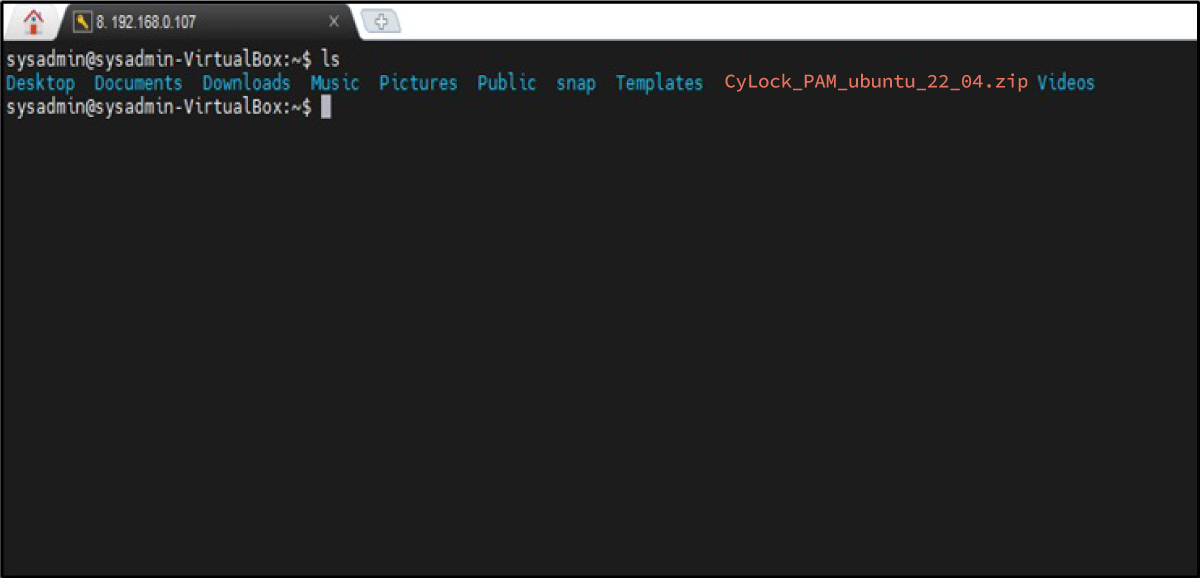
Figure 6: CyLock MFA PAM module for Ubuntu is uploaded in the server
sudo unzip CyLock_PAM_Ubuntu_22_04.zip
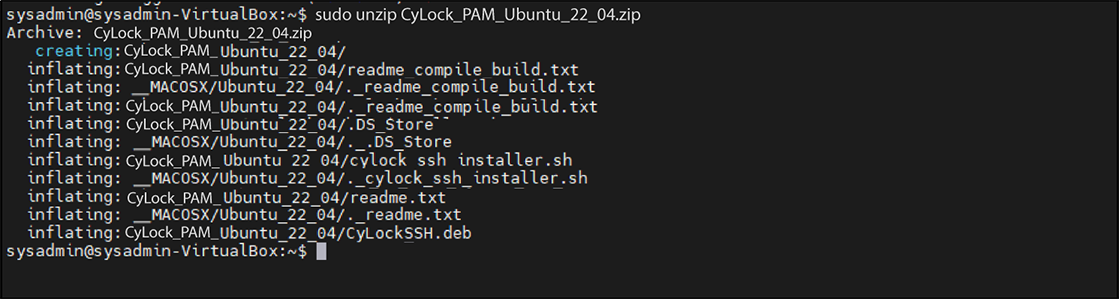
Figure 7: Unzip the CyLock MFA PAM module
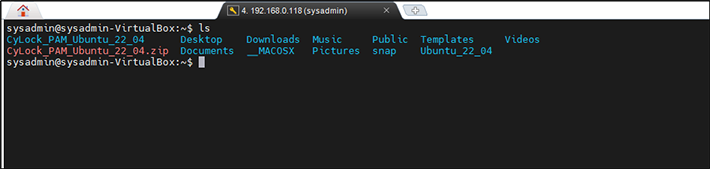
Figure 8: Unzipped Folder
sudo chmod a+x *.sh
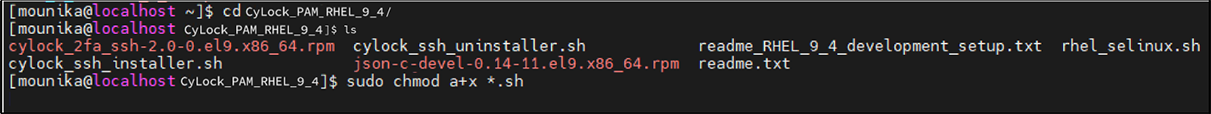
Figure 9: Giving executable permission to the installer file
sudo ./cylock_ssh_installer.sh
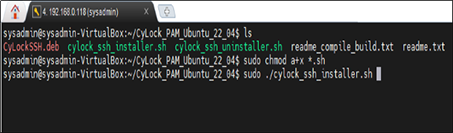
Figure 10: Running the CyLock PAM installer
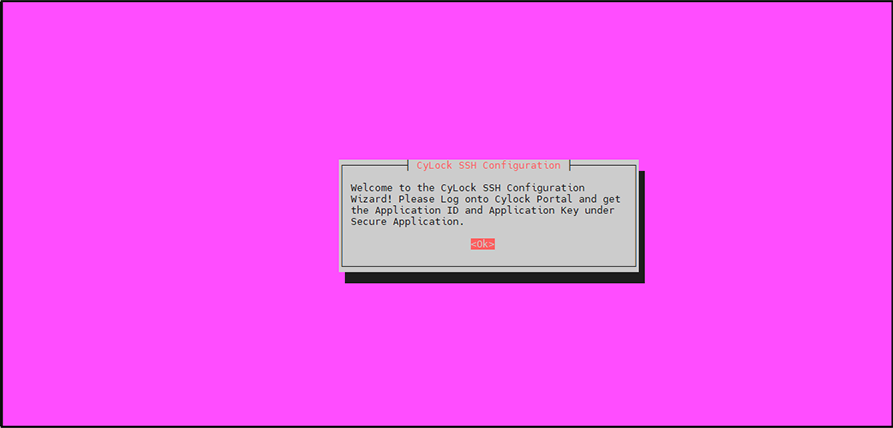
Figure 11: CyLock SSH Configuration setup wizard
Enter the CyLock Auth Server URL and click OK, as shown in the Figure 12.
Note: Contact CyLock Support Team to get CyLock Auth Server URL.
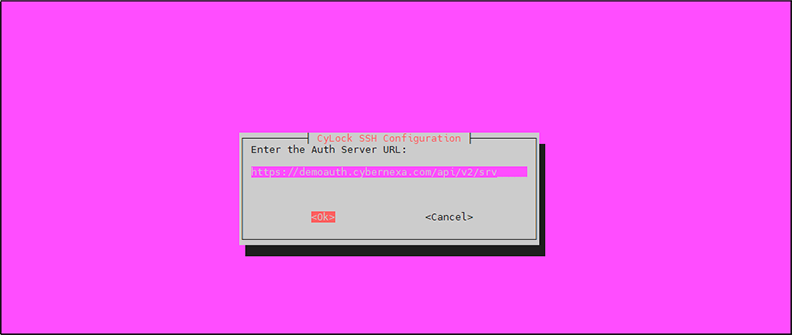
Figure 12: Entering Auth Server URL
Copy and paste the Application Key that was generated after securing the SSH Application in the CyLock portal and click OK.
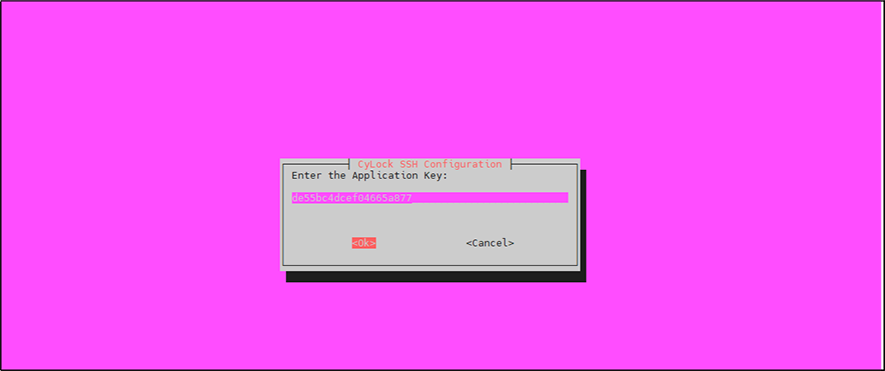
Figure 13: Entering Application Key
Copy and paste the Authorization ID that was generated after securing the SSH Application in the CyLock portal and click OK.
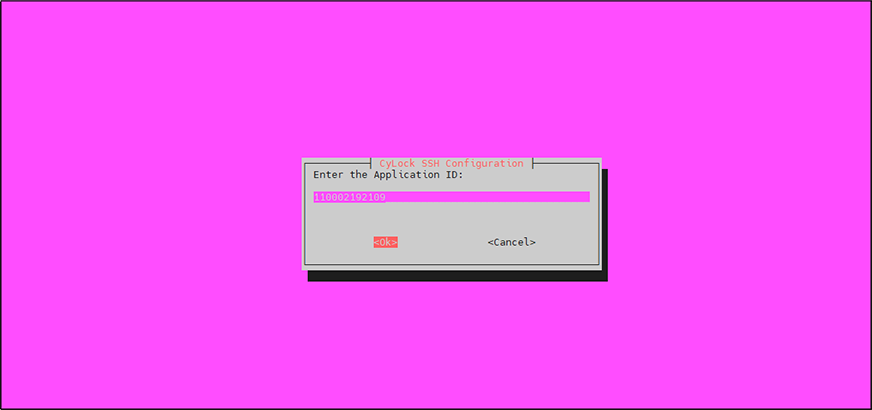
Figure 14: Entering Application ID
Set the Default Authentication option (YES / NO) of your choice:
Click OK to proceed.
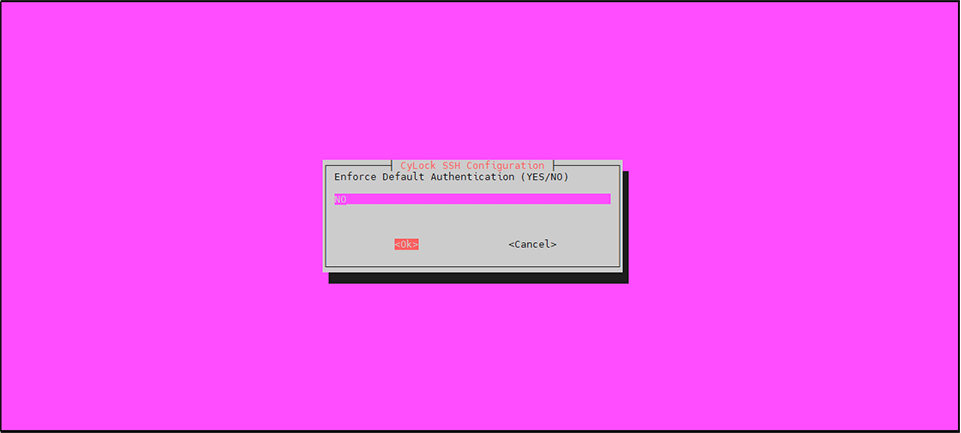
Figure 15: Setting Default Authentication
Set the Fail mode (ALLOW / DENY) of your choice:
Click OK to proceed.
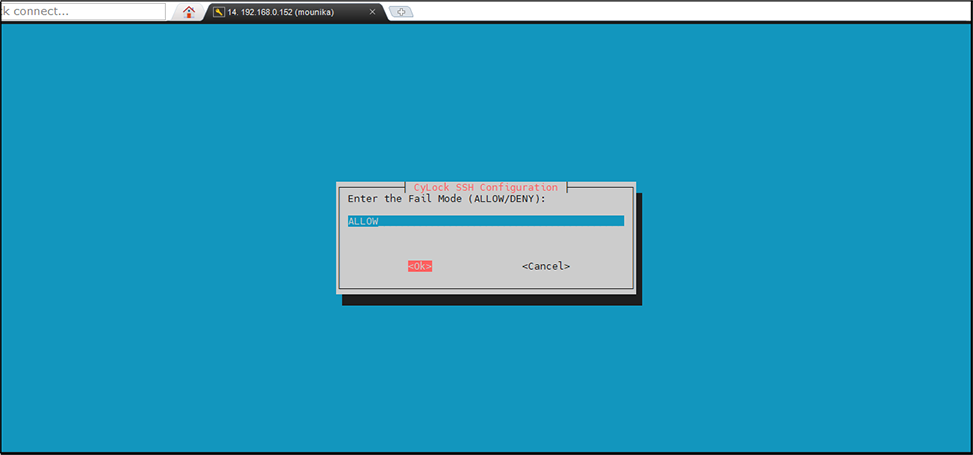
Figure 16: Setting Fail mode
Set whether you want to ALLOW or DENY Device Registration:
Click OK to proceed.
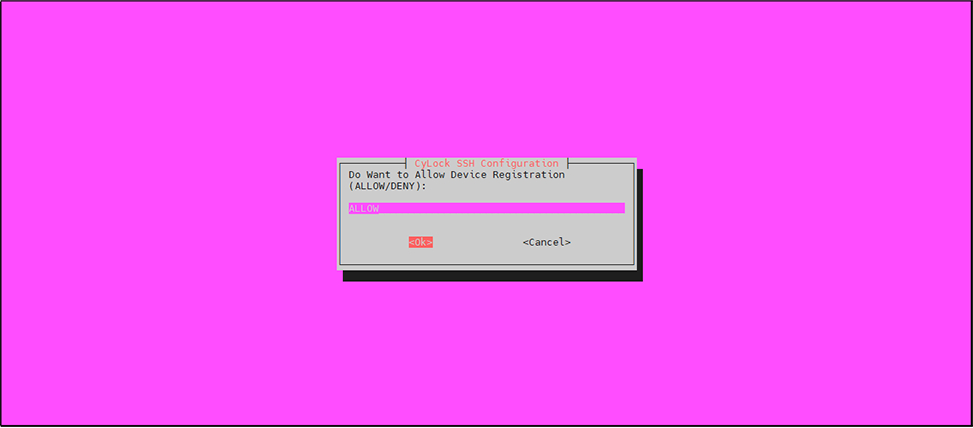
Figure 17: Setting Device Registration
Once the CyLock SSH Configuration set up wizard is completed, you will get ‘Installation and configuration completed successfully ‘success message as shown in the Figure 18.
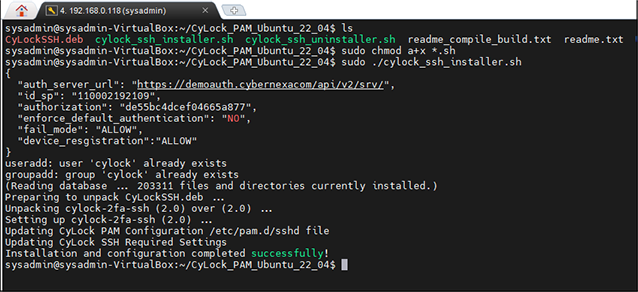
Figure 18: PAM module installed successfully
Test the Set up
Now, attempt to log in to your server. After the first factor (1FA) is successfully verified, the second factor (2FA) will be triggered based on the user's default authentication method. Since the default authentication mode is set to 'NO,' you will be presented with multiple authentication options, as shown in the Figure 19. You can select any of these modes to complete the 2FA and gain access to Ubuntu server.
Supported Authentication options for SSH Login:
CyLock MFA Supports the below Authentication options to login Ubuntu server through SSH.
_Ubuntu.png)
Figure 19: From List of supported Authentication modes, selected online (push)
You will receive a push notification to your registered mobile as shown in the Figure 20.
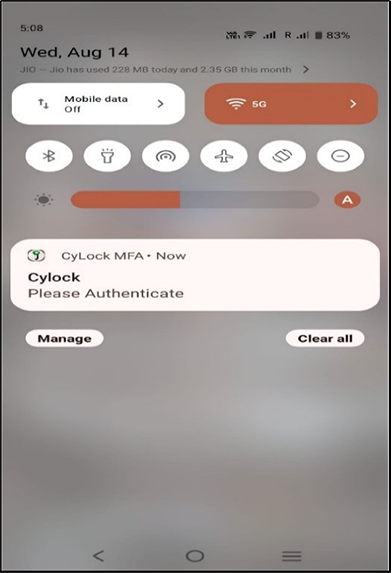
Figure 20 : Received Push Notification in registered mobile
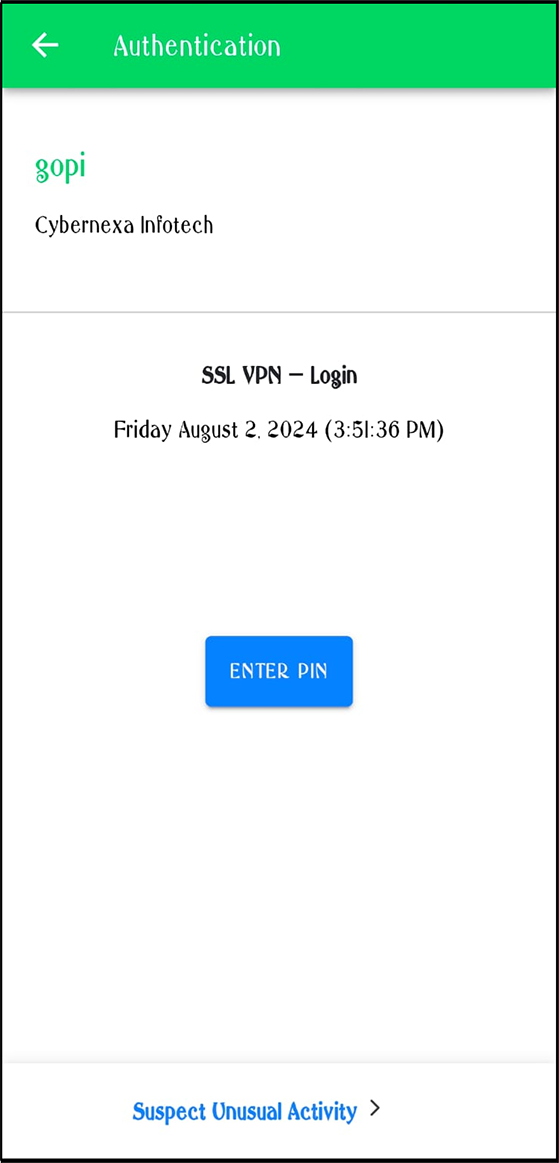
Figure 21: Clicking on Enter PIN

Figure 22: Enter PIN prompt
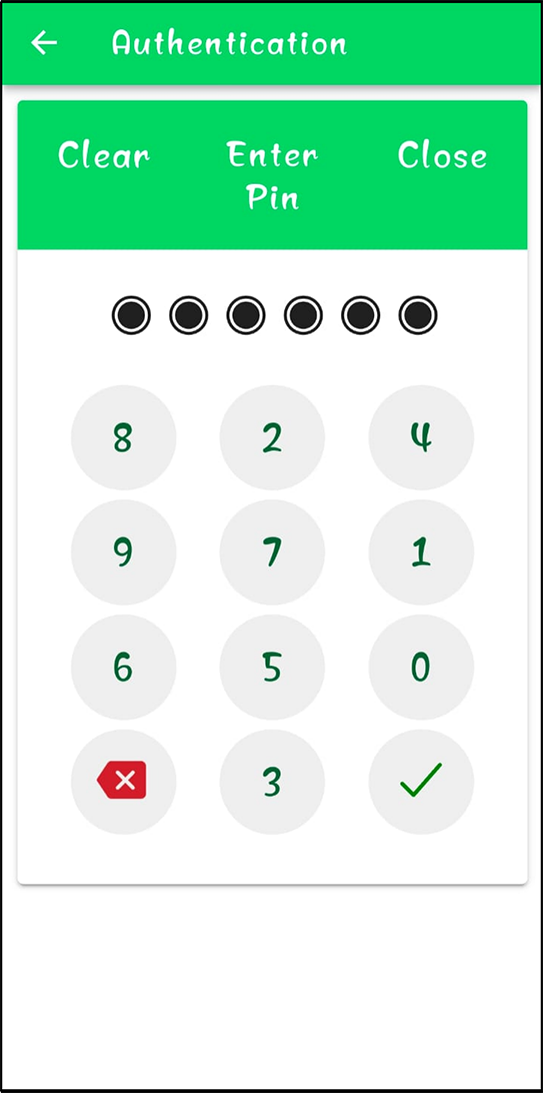
Figure 23: Entering the 6 digit PIN
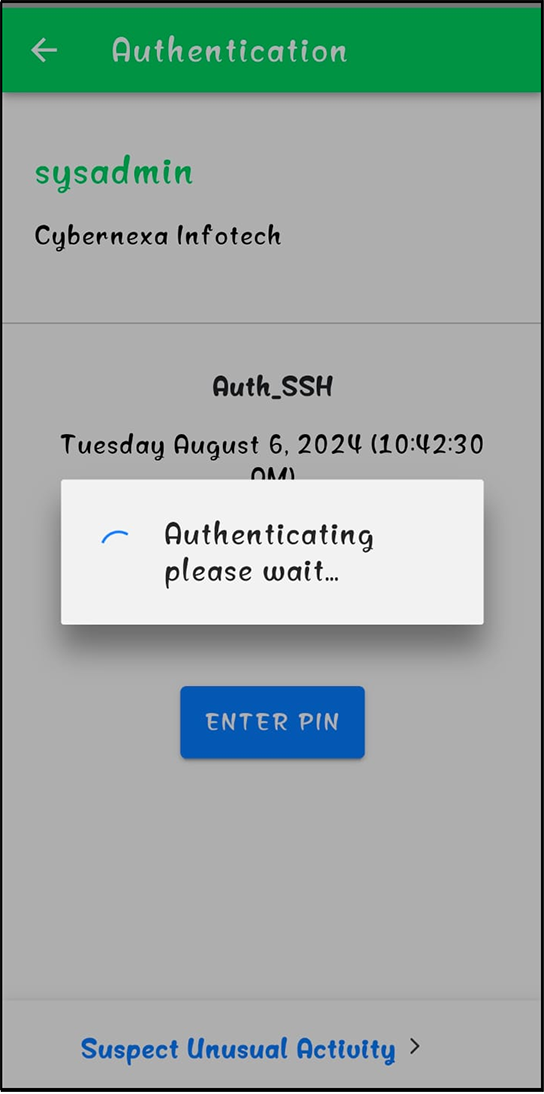
Figure 24: Authentication processing
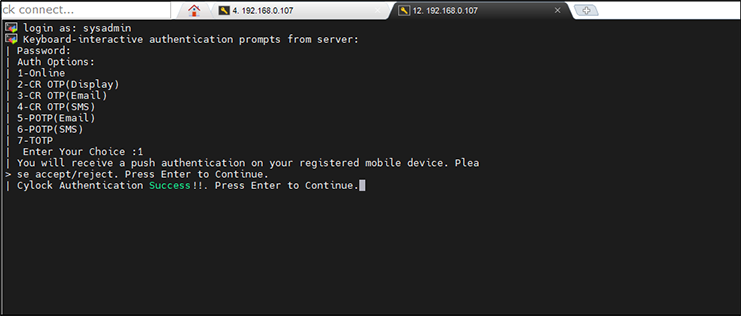
Figure 25: Authentication Success message
Now you can do SSH Login to the Ubuntu server successfully using CyLock MFA.
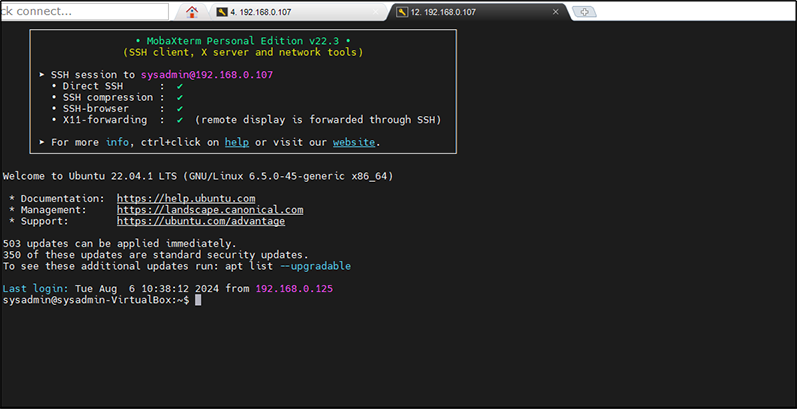
Figure 26: Successfully done SSH Login to the Ubuntu server